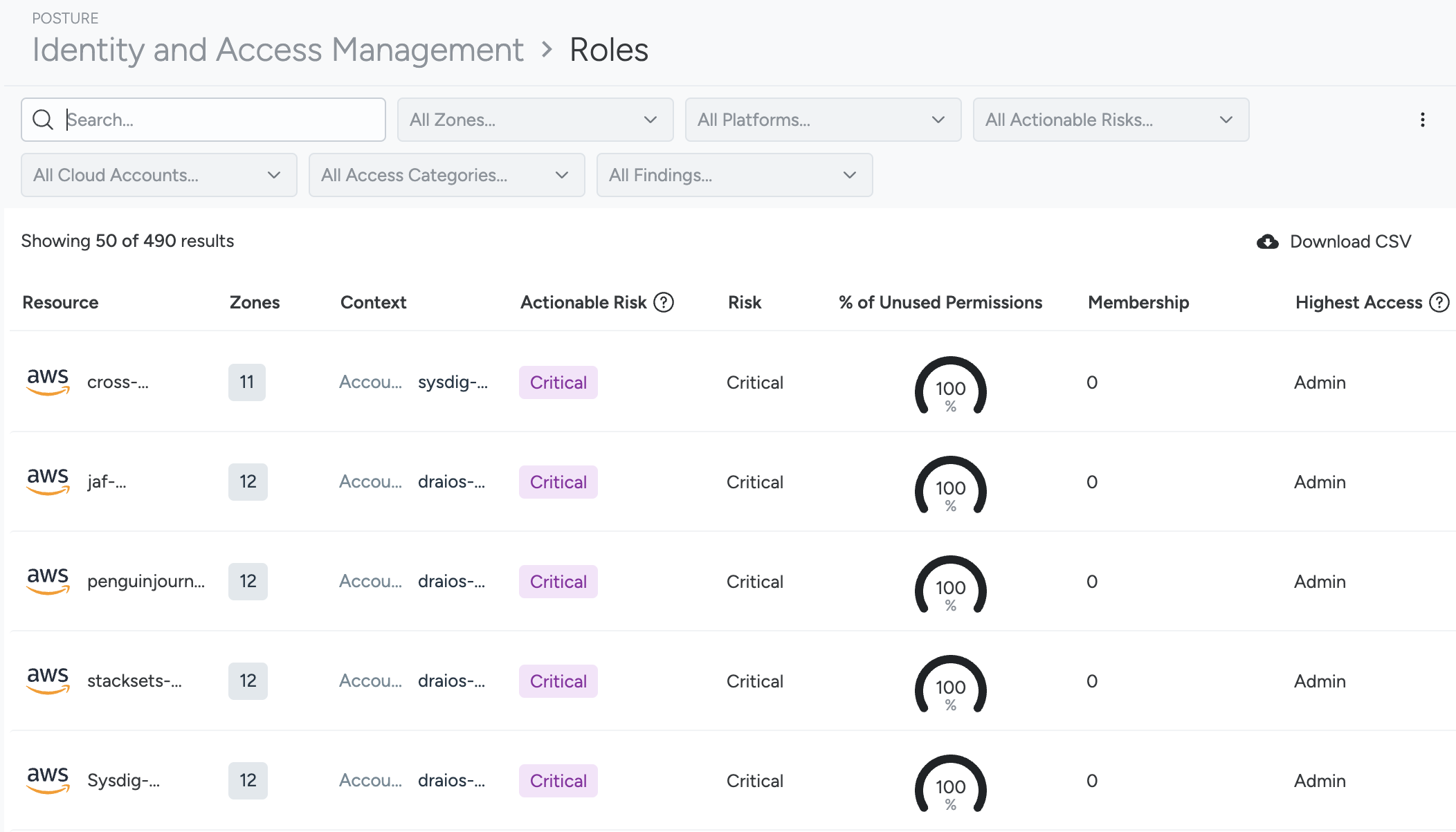
Roles
Filter and Sort Roles
Use the sortable columns to organize and filter roles for assessing identity risks. You can sort roles based on the following criteria:
Unused Permission Criticality
Unused Permission Criticality focuses on unused permissions, while Permission Criticality looks at all permissions. Unused Permission Criticality is designed to help you achieve Least Permissive access.
Values: Critical, High, Medium, Low
Risk
This is a calculation of risk based on all permissions. See Understanding Risk Scoring for more information.
Values: Critical, High, Medium, Low
% of Unused Permissions
This shows the number of unused permissions used with the role, per total permissions assigned to the role, shown as a percentage graph.
When remediating, immediately target the roles with the greatest exposure and refine them according to the suggestions.
Membership
For AWS, this reflects the number of users who can use this role.
For GCP, the membership number reflects the number of users, groups, and/or service accounts who are bound to this role.
Highest Access
Values:
- Admin: Admin access granted
- Write: Write access granted
- Read: Read access granted
- Empty Access: No permissions are granted at all
For more information, see Understand Highest Access.
Findings
A finding in Cloud Infrastructure Entitlement Management (CIEM) indicates poor security hygiene, either due to misconfiguration or inadequate identity security practices. The findings on Roles pages include:
AdminInactive
Available Filters
- Search: Free text search on terms in the resource name
- Platform: by provider, e.g. AWS
- Unused Permission Criticalities: By severity
- Cloud Accounts: Account name/number by cloud provider (e.g. AWS)
- Access Categories:
Admin,Write,Read, orEmpty Access - Findings:
Admin,Inactive
Next Steps
Feedback
Was this page helpful?
Glad to hear it! Please tell us how we can improve.
Sorry to hear that. Please tell us how we can improve.