Home
For the Home page dashboards to display data, ensure that you complete basic onboarding and connect at least one data source; otherwise, the page provides prompts to complete the setup tasks.
Check the Data Source Status
You can view and check a status summary of data sources at the top right of the page. These include:
- Detected cloud accounts
- Sysdig agents status, based on nodes where agents have been or could be deployed.
View Cloud Accounts
Select the AWS, GCP,or Azure icon to connect a cloud account, or to see the status of connected accounts.
For connected accounts, you can see:
- The number of accounts, projects, or subscriptions connected
- The connection status of the cluster
- A link to the Data Sources page, where you can take action
View Sysdig Agents
Select the Sysdig Agents icon to see:
- The number of agents connected
- The nodes that require attention because their agents are out of date or almost out of date
- The agent status
- A link to the Data Sources page, where you can take action
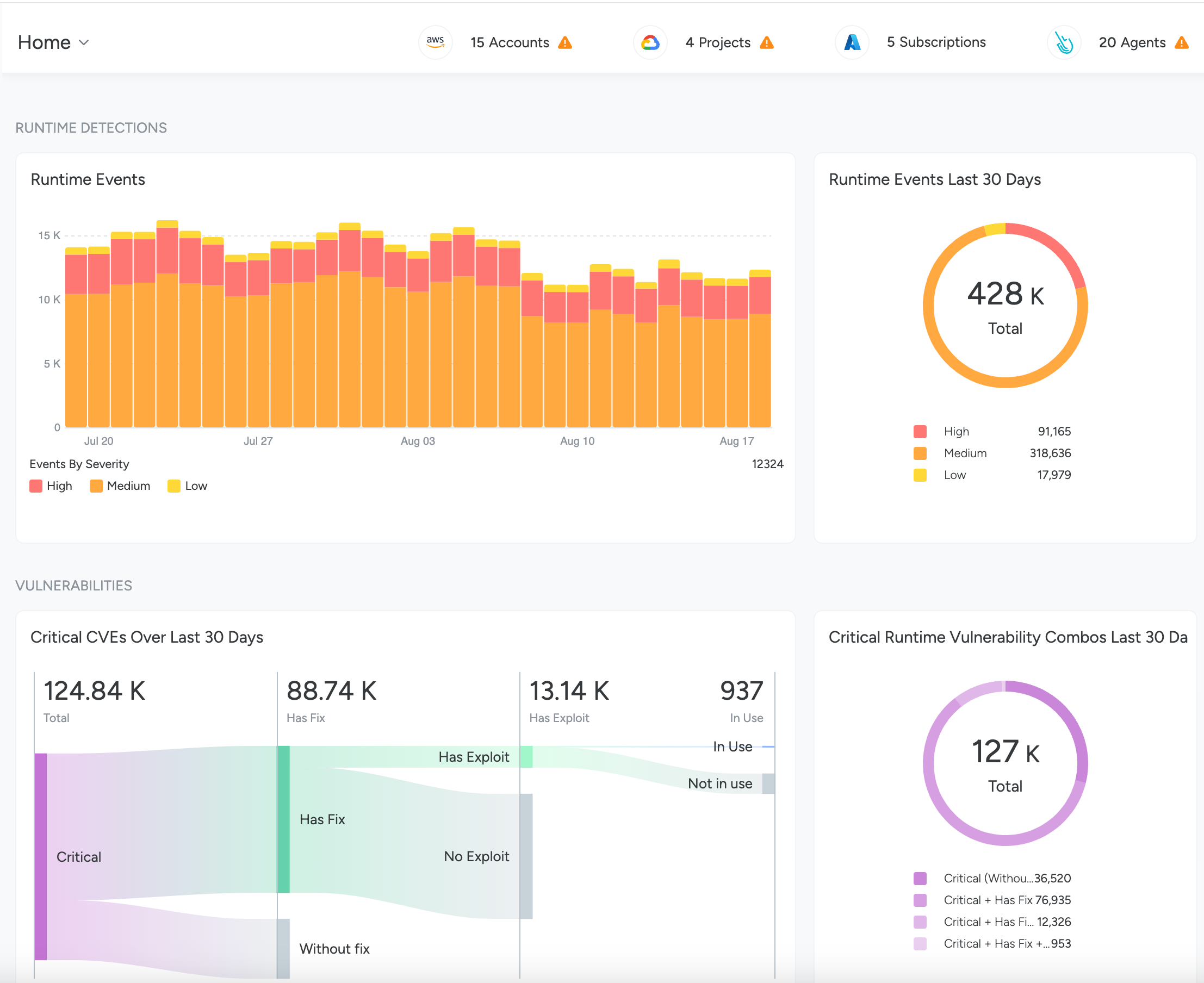
View Runtime Events
After you set up Threat Detection using either the Sysdig Agent or Agentless Threat Detection, you can view Runtime event trends broken down by Severity in this section.
Check Vulnerabilities
You can view various charts in this section based on the scanning you set up in your environment, such as:
- runtime scanner
- host scanner
- pipeline scanning
- registry scanning
- agentless scanning
The charts highlight the most critical vulnerabilities in your environment.
Posture
To view posture data, you should set up at least one of the following: CSPM, KSPM, or CIEM.
Depending on what is installed, you can view a breakdown of your evaluated resources by category, trends of unused permissions, poor identity hygiene practices, and trends of passing compliance requirements for your starred policies.
You can change starred policies/compliance trends on the Compliance page.
If you have not starred any policies as favorites, then the line graph displays the results from the three policies with the lowest passing scores.
Feedback
Was this page helpful?
Glad to hear it! Please tell us how we can improve.
Sorry to hear that. Please tell us how we can improve.