Install Host Shield on Windows
Installation Requirements
Prerequisites
- Windows Server 2019 or Windows Server 2022.
ACCESS_KEY: The agent access key.REGION:us1,us2,us4,au1,eu1,me2,in1. For more information, see Sysdig SaaS regionCOLLECTOR: Use the collector address for your region. For more information, see SaaS Regions and IP Ranges.- Administrator permissions to perform the operations.
Coverage Map
| Platform | Threat Detection and Response | Vulnerability Management | Posture Management |
|---|---|---|---|
| Windows Server 2019 | ✅ | ✅ (Host Only) | ✅ |
| Windows Server 2022 | ✅ | ✅ (Host Only) | ✅ |
| Windows Server 2025 | ✅ | ✅ (Host Only) | ❌ |
Install the Windows Host Shield
You can install the Windows Host Shield using an MSI, which supports both GUI and CLI operation. Download the MSI package from the Sysdig download center.
GUI Installation
You can execute the MSI using a GUI and the installation process will prompt you to accept the EULA and enable the following applications Vulnerability Management and Posture Management.
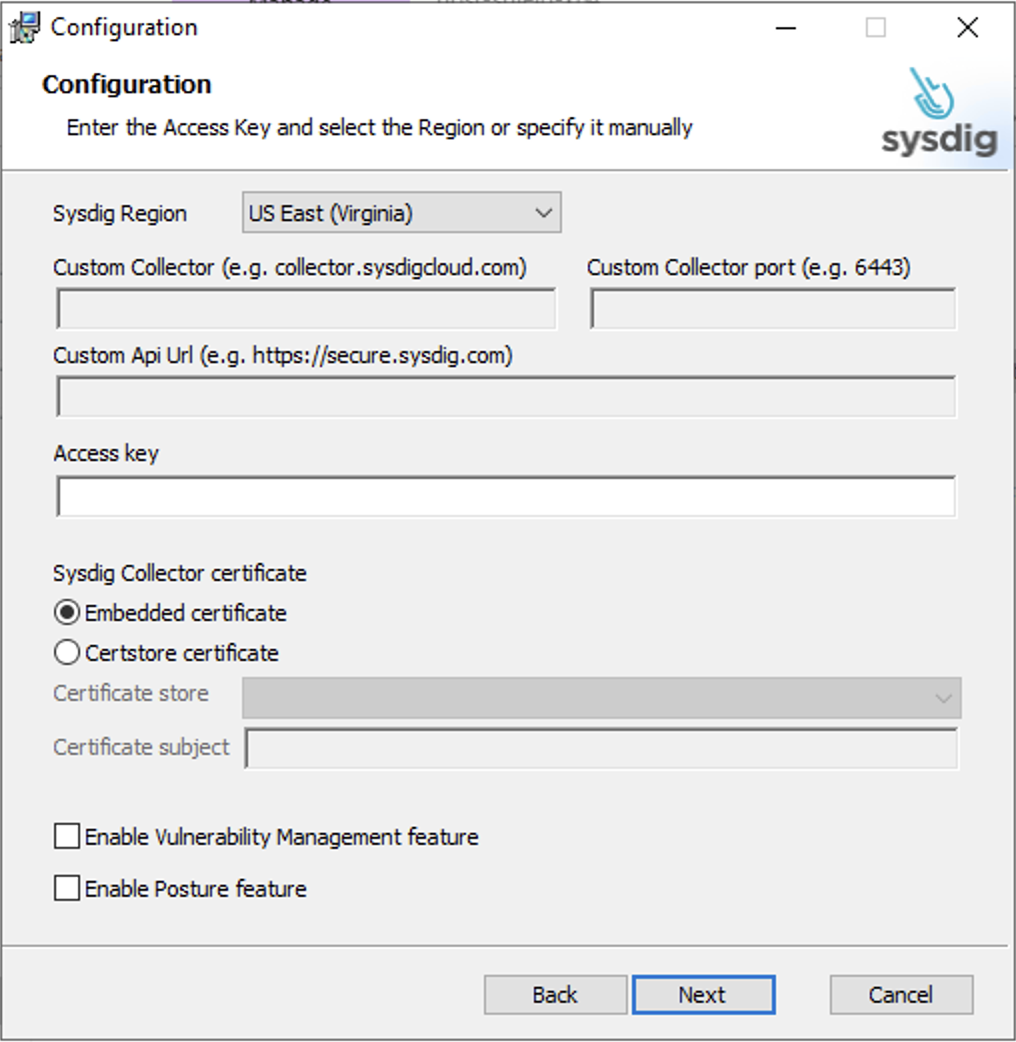
CLI Installation and Configuration
Run the MSI in silent mode via CommandLine or PowerShell:
msiexec /i sysdig-host-shield.msi REGION=<region> ACCESS_KEY=<AGENT_ACCESS_KEY> VM_FEATURE_ENABLED=False POSTURE_FEATURE_ENABLED=False ACCEPT_TERMS_CONDITIONS=True /qn
Using Certificate Storage
Windows stores certificates locally in a storage location called the certificate store. This store may contain multiple certificates issued by different Certification Authorities (CAs).
To configure Sysdig Host Shield for certificate storage, set the following environment variables:
COLLECTOR_CERT=Certstore: Enables certificate storage usageCOLLECTOR_CERTSTORE_NAME=<store_name>: Specifies the certificate store to use. Choose from:MY: Personal storeROOT: Trusted Root Certification AuthoritiesCA: Intermediate Certification AuthoritiesSPC: Software Publisher Certificates
COLLECTOR_CERT_SUBJECT=<certificate_subject>: Specifies the Common Name (CN) of the certificate. This can be a full or partial string match.
Example Configuration:
COLLECTOR_CERT=Certstore
COLLECTOR_CERTSTORE_NAME=MY
COLLECTOR_CERT_SUBJECT=SysdigAgentCert
Using Custom Collector
If you’re not using one of the following SaaS Regions, you must provide REGION=custom and the following variables:
COLLECTOR_URL: Specifies the custom collector host (for example,your.custom.host.com)COLLECTOR_PORT: Specifies the custom collector port (for example,6443)API_URL: Specifies the custom api url (for example,https://your.custom.host.com)
By setting ACCEPT_TERMS_CONDITIONS to True, you acknowledge and expressly agree that your use of or access to the Sysdig software is governed by the applicable terms and conditions located at Sysdig Legal Terms unless otherwise stated in a Sysdig Order Form or other written mutual agreement between Customer and Sysdig.
Proxy Settings
If your environment requires internet access through a proxy server, you can configure proxy settings in the host-shield.yaml file. These settings ensure that Sysdig Host can communicate with Sysdig.
proxy:
http_proxy: http://customer-proxy
https_proxy: http://customer-proxy
After applying the changes, restart the Host Shield Windows service by running the following command from the PowerShell terminal:
$ Restart-Service SysdigHostShield
Antivirus and EDR Exceptions
Sysdig Windows Host Shield may conflict when coexisting with Antivirus software or Endpoint Detection and Response (EDR) sensors. To prevent termination of the Sysdig Windows Host Shield processes, it is recommended to set up exclusions for the Host Shield root installation directory.
Carbon Black Cloud
- From the Carbon Black Cloud Console go to Enforce > Policies.
- Select the desired Policy and click on the Prevention tab.
- Add a new
Permissionby clicking on the+sign. - Add a new application path in the
Permissionssection and provide the directory exclusion*:\Program Files\Sysdig\Shield\**. - Check
Bypassoption box forPerforms Any Operation. - Click Confirm.
Windows Defender
- Open Windows Security > Virus & threat protection.
- Under Virus and threat protection settings, select Manage Settings.
- Under Exclusions select Add or remove exclusions.
- Click on the Add an exclusion button and choose Folder.
- Browse the drive where the Sysdig Windows Host Shield was installed, and select the
Program Files\Sysdig\Shielddirectory.