Posture Controls
- To know precisely what has been or will be evaluated
- To review a specific control to see its logic and remediation
- To edit control parameters to tune your compliance results and personalize evaluation parameters
Sysdig Posture Controls are built on the Open Policy Agent (OPA) engine, using OPA’s policy language, Rego. The Posture Controls library exposes the code used to create the controls and the inputs they evaluate, providing full visibility into their logic. You can download the code as a JSON file.
For details, see external documentation on:
Prerequisites
This feature requires the Compliance component.
If necessary, review:
How Controls are Structured
Sysdig controls are built on the Open Policy Agent (OPA) engine, using the OPA policy language, Rego. The Posture Controls library exposes the code used to create the controls and the inputs they evaluate, providing full visibility into their logic. You can download the code as a JSON file.
For details, see the Open Policy Agent (OPA) and Rego external documentation.
Navigate Posture Controls List
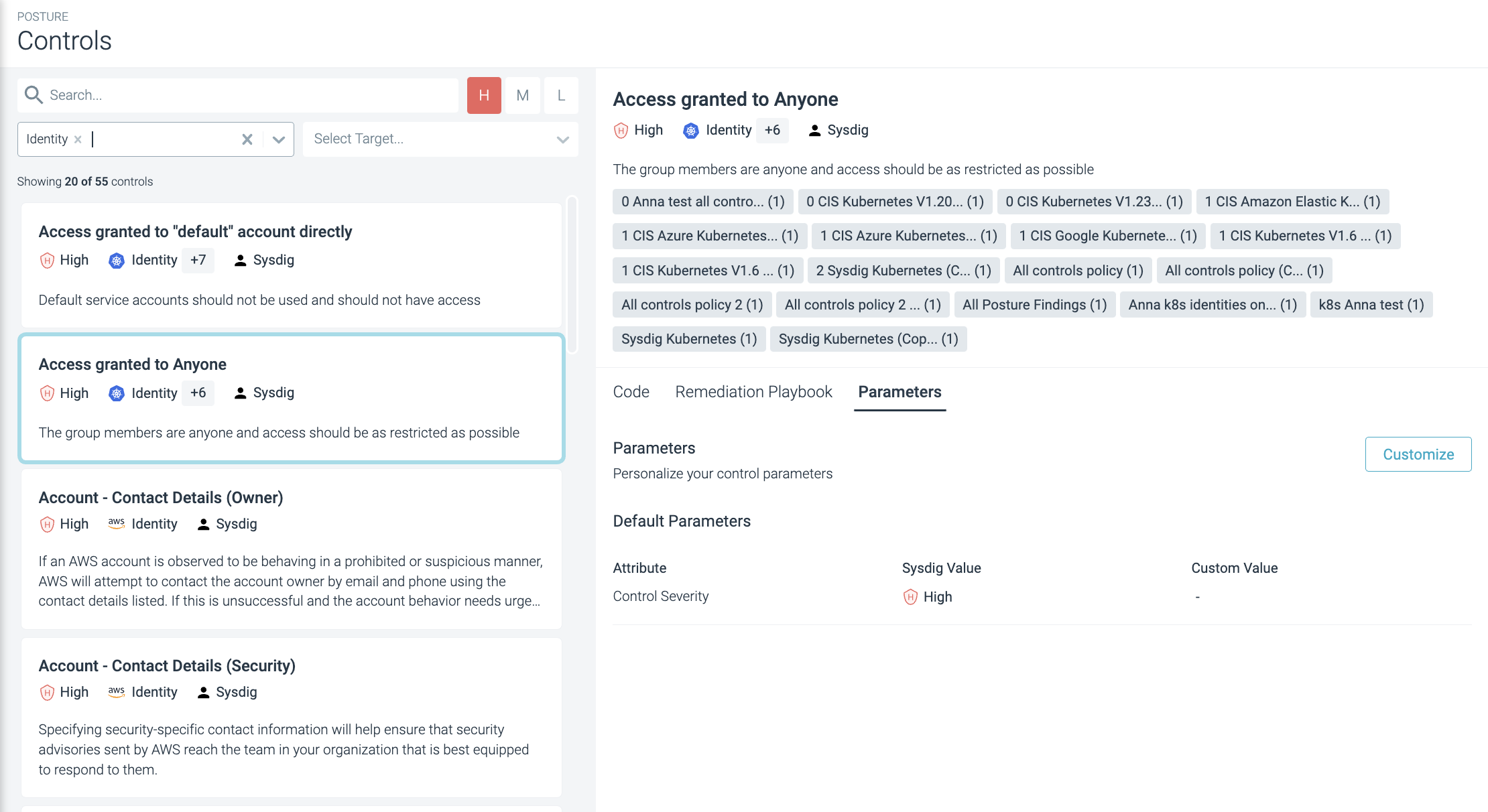
To see the Posture Controls list, select Policies > Posture | Controls.
Select a specific control to open details in the right panel.
Search and Filter the List
Find specific controls through search and several filter options.
- Search: Enter any word or part of a word in the name, description, or author to find matching controls.
- Severity: Filter controls by their severity level; High, Medium, or Low.
- Select Type: From the drop-down, choose a control type such as Cluster, Host, Identity, or Resource.
- Select Target: The specific platforms, distributions, and supported versions against which a control evaluates resources. Online cloud platforms, such as Azure Kubernetes Service (AKS), Amazon Web Services (AWS), and Google Cloud Platform (GCP), do not have versioning but always relate to the latest version.
Stack multiple parameters to create more specific filter expressions.
Add multiple parameters to create more specific filter expressions.
Review a Control
Select a specific control.
Review basic attributes. At the top of the right panel you can see:
Control title: Title of the Control
Severity: H, M, L
Type: Cluster, Host, Identity, Resource
Author: For example, Sysdig for out-of-the-box controls
Description: Meaningful description for the control.
Policies: The policies to which the control is linked.
Hover over the policy names to get full details, such as the exact requirement number for the particular compliance standard, and to navigate to that requirement in the policy details page.
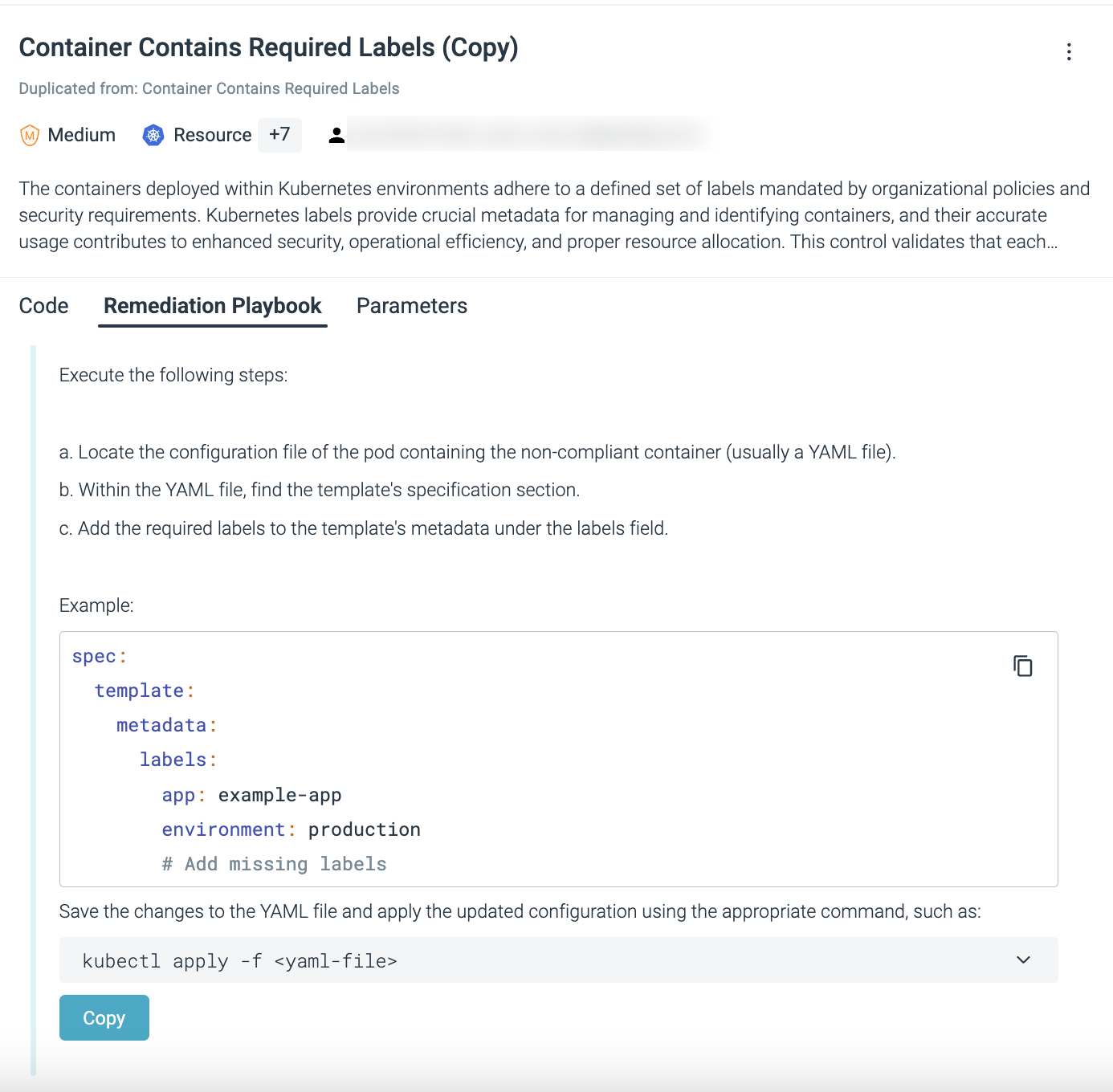
Code: Use the provided code snippets.
The code provides visibility into the precise objects that are evaluated and how the evaluation rules are structured. The display includes Inputs (where applicable) and the evaluation code written in Rego.
You can copy and download the code as a
.jsonfile.Remediation Playbook: Review the recommended steps in the Remediation Playbook to resolve failing controls. Sometimes, you must provide the applicable input in the provided remediation code.
Configure Parameters: Edit the assigned Severity of a control. For some controls, edit other evaluation parameter values.
Customize Posture Control
Sysdig incrementally adds the ability to customize posture control by adding parameters defined within posture controls.
Configure Severity
By default, Sysdig assigns an opinionated severity level to the posture controls it delivers.
To edit the Severity assignment:
Select a specific control and select the Parameters tab.
Click Customize.
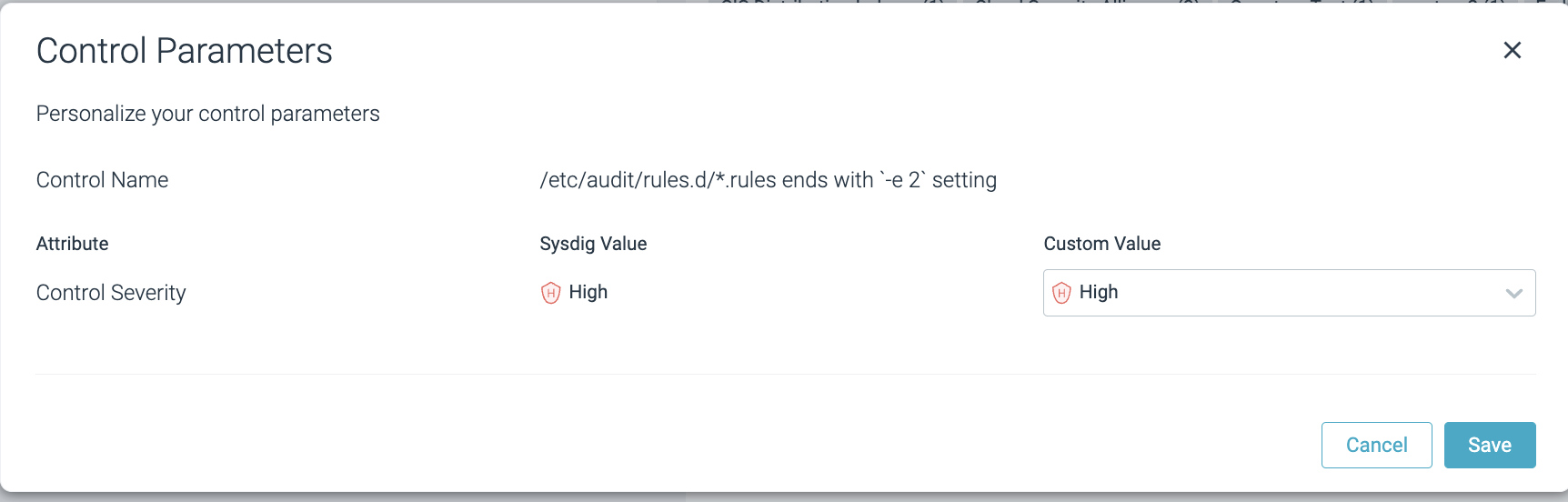
Choose the Severity level, and click Save.
A success message appears. The Compliance results will be updated during the next evaluation.
You can duplicate a control and assign two different severities if it suits your use case.
Configure Evaluation Parameters
Select a specific control and select the Parameters tab.
Click Customize.
Customize an evaluation parameter.
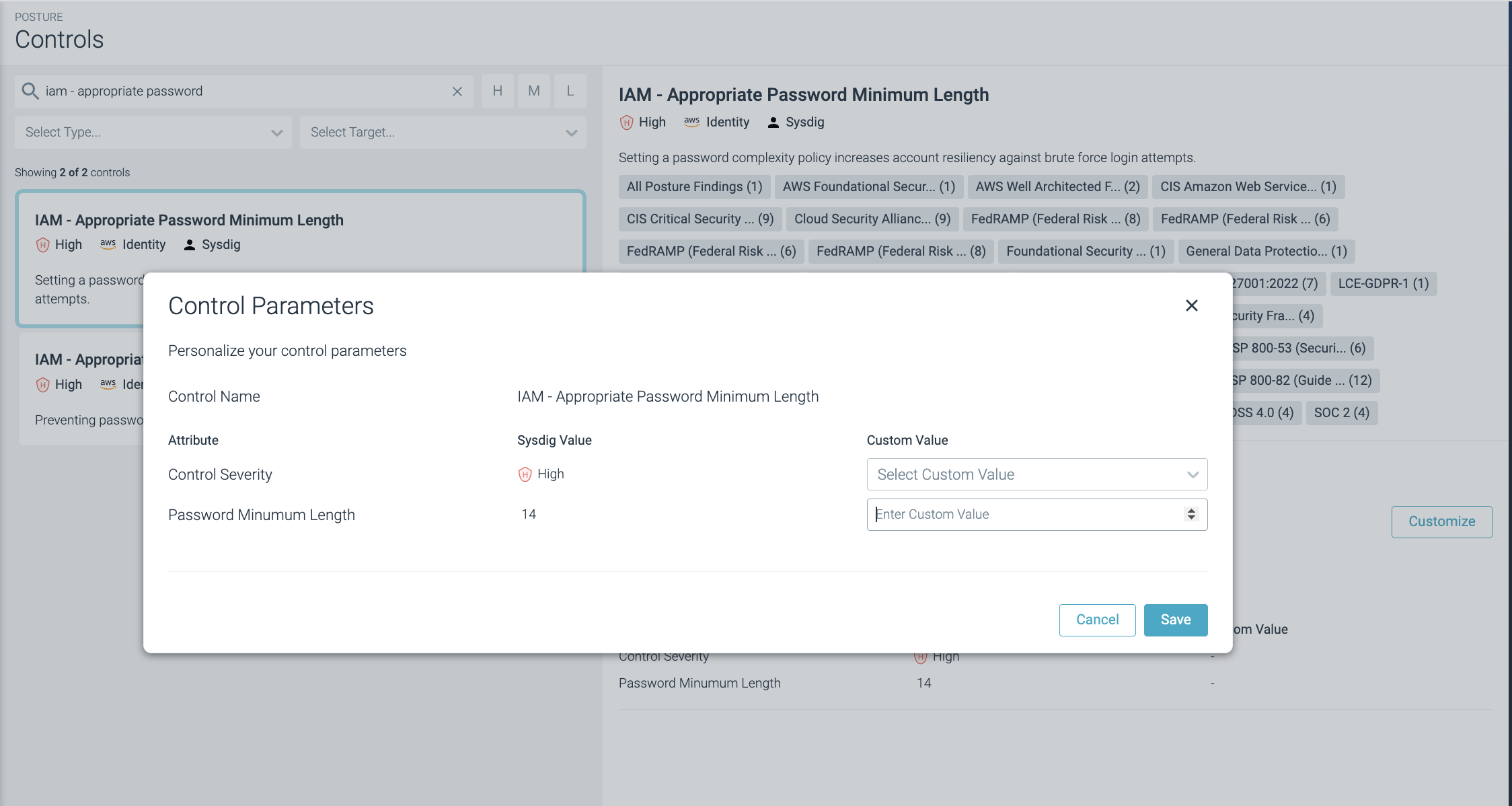
- Click Save.
Customize Labels
Currently, custom labels can be added or deleted from controls if labels were present in the original control.
Select a control that contains labels and open the Parameters tab.
Click Customize.
Enter a label in key:value or key format, such as
env:prodorowner.Click Return.
If you want to add another label, insert a comma and the next label and click Return again.
Click Save when your list is complete.
The labels are displayed as Custom Values in the Parameters tab.
To include custom labels in the Remediation Playbook YAML, you must download the sample code and enter the created labels manually.
Custom Controls
You can now duplicate and edit any control. For example, you can create a new custom control that checks for a specific label.
Guidelines
- You cannot link a user-duplicated control to an out-of-the-box policy.
- You can use a control from one policy in another custom policy with different parameter values. Even a change in severity level constitutes a different use case.
- You can delete or edit a duplicated (custom) control.
- Best practice: Establish naming conventions to make searching for custom controls in the Control List easy.
Duplicate a Control
Select Policies > Posture > Controls and browse or search for a specific control.
Example: If a control contains labels, the default Control Name includes the word Label. Search on
labelto find these controls and duplicate them if desired.Right-click the three-dot menu and select Duplicate.
Edit the following as desired and click Save:
Name: By default, Sysdig creates the Original Control Name (copy). You can enter any name that is not used by any other existing control.
Description: Optionally, enter a meaningful description about the control.
Severity: You can select a severity for your custom control.
If the original control contained configurable evaluation parameters, you can customize them.
You can now link the new custom control to a requirement in your custom policies.
Edit or Delete Custom Controls
Select a custom control from the Control List.
Tip: Look for the Author to identify custom controls. If the author is not
Sysdig, then the control is custom.To edit: From the 3-dot menu, select Edit, change the Control Details (Name/Description/Severity) as needed, and click Save.
The changed details will be applied to any custom policy where the control is used after the next evaluation.
To delete: From the 3-dot menu, select Delete and confirm after the warning, Yes, Delete.
The Compliance and Posture results of evaluations made from this control and any accepted risks for the control are deleted upon the next evaluation.
Customizable Default Controls
The following controls are now customizable and have evaluation parameters that could be configured to personalize posture controls for specific use cases:
AWS
- API Gateway - Gateway with VPC_LINK connection type
- API Gateway - REST API Gateway Stage with unencrypted cache
- API Gateway - Rest API Gateway Stage without required tag
- API Gateway - Rest API Gateway without required tag
- API Gateway - Stage without required ACL
- AutoScaling - App-Tier Auto Scaling Group with associated Elastic Load Balancer
- AutoScaling - Auto Scaling Group Cooldown Period
- CloudFront - Use CloudFront Content Distribution Network
- ECR - Restricted User Access
- ElastiCache - Valid Node Type
- ElastiCache - Latest MemCached Engine Version
- ElastiCache - Latest Redis Engine Version'
- ElastiCache - Latest Instance Generation
- ElastiCache - Appropriate Cluster Cache Nodes Count
- ElastiCache - Expiration of Lease for Reserved Cache Node
- ElastiCache - Recent Acquisitions of Reserved Cache Nodes
- IAM - Appropriate Access Key Rotation
- IAM - Appropriate Password Minimum Length
- IAM - Appropriate Password Reuse
- IAM - No Unused Passwords
- IAM - No Unused Access Keys
- IAM - Unused Root Account
- Lambda - Function Uses Supported Runtime
- Lambda - Lambda Cross Account Access
- Networking - Defined Compliant destination-cidr-block in Routing Tables
- Resource Contains Required Labels
- SNS - Appropriate Subscribers
- SNS - Cross Account Access
- S3 - Enabled Encryption At Rest
GCP
- GCR - Restricted User Access
- Project - Corporate Credentials
Azure
- ACR - Restricted User Access
- AppService - Enabled Java Autoupdate
- AppService - Required Latest PHP Version
- AppService - Required Latest Python Version
- AppService - Required Latest TLS Version
- Compute - Installed Endpoint Protection
- Logging - Appropriate Diagnostic Setting
- Networking - Appropriate Flow Retention Setting
- PostgreSQL - Appropriate Log Retention Setting
- SQL Server - Appropriate Auditing Retention
Kubernetes
- ACR - Approved Registries
- API Server - Access to Pod Spec (OCP4)
- API Server - Defined audit-log-maxage
- API Server - Defined audit-log-maxbackup
- API Server - Defined audit-log-maxsize
- API Server - Owner of Pod Spec (OCP4)
- Approved Registries
- Container Contains Required Labels (new control)
- Container with Forbidden Capabilities (new control)
- GCR - Approved Registries
- Kubelet - Appropriate event-qps Level
Feedback
Was this page helpful?
Glad to hear it! Please tell us how we can improve.
Sorry to hear that. Please tell us how we can improve.