Sysdig MCP Server Integration
For up-to-date information, refer to the Sysdig MCP Server GitHub repository. This documentation is based on version 0.1.1.
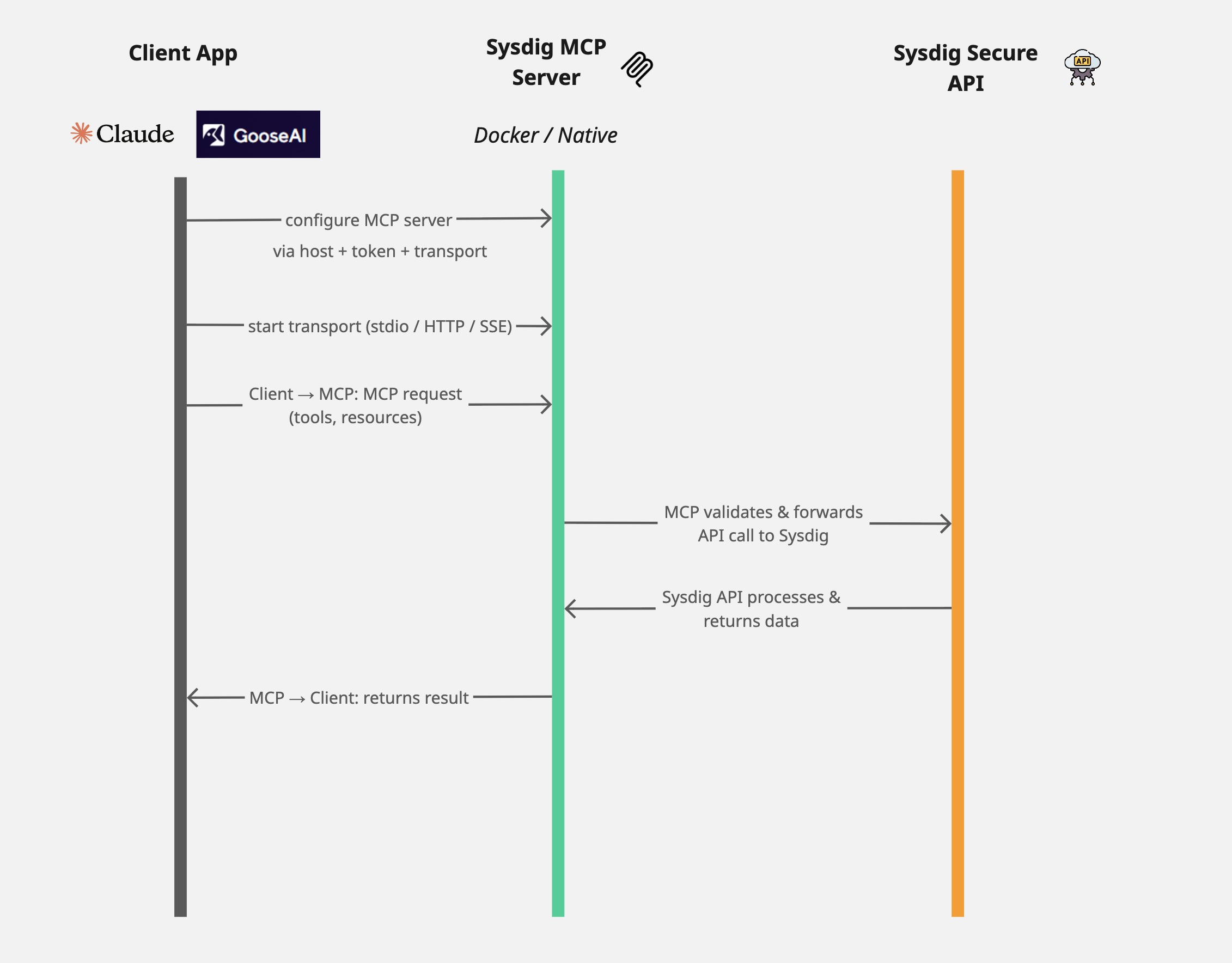
The Sysdig MCP Server bridges AI workflows and the Sysdig API, exposing tools, resources, and contextual data for informed AI-driven actions.
It enables AI clients to:
- Query Sysdig Secure for runtime security events
- Retrieve process trees and event metadata
- Generate and execute SysQL queries via natural language
- Invoke Sysdig CLI scanning tools (when supported)
- Tie together AI prompts, context, and Sysdig data to assist decision-making
It acts as an intermediary: clients speak MCP to your MCP server, which then calls the Sysdig APIs (or CLI) as needed to fulfill requests.
Features
The server currently supports the following capabilities:
| Feature | Description | Example Prompt |
|---|---|---|
get_event_info | Get full details about a specific security event | “Retrieve full details for event ID abc123” |
list_runtime_events | List runtime security events, with optional filters | “Show me high severity events in the last 2 hours in cluster1” |
get_event_process_tree | Retrieve a process tree for a given event | “Get the process tree for event ID xyz789” |
generate_and_run_sysql | Translate natural language to SysQL and execute | “List top 10 pods by memory usage in the last hour” |
run_sysql | Execute a pre-written SysQL query directly (use only when user provides explicit query) | MATCH CloudResource WHERE type = 'aws_s3_bucket' LIMIT 10 |
run_sysdig_cli_scanner | Use Sysdig CLI scanner for vulnerability or IaC analysis (on stdio transport) | “Scan image ubuntu:latest for vulnerabilities” |
The run_sysdig_cli_scanner tool is only available when using the stdio transport (that is, local usage).
It may not be available over HTTP or streaming transports.
Prerequisites
- Python 3.10+ (or as specified in the project)
- Access to a Sysdig Secure instance with an API token
- Network connectivity from the MCP server to Sysdig
- (Optional) Docker for deployment
- For native/host runs: dependencies listed in
pyproject.toml
Development Setup
Using uv
You can use uv as a drop-in replacement for pip to create the virtual environment and install dependencies.
If you don’t have uv installed, follow the instructions on the uv project page.
To set up your local environment:
uv venv
source .venv/bin/activate
This creates a virtual environment using uv and installs the required dependencies.
Configuration
API Token
To authenticate with the Sysdig Secure platform, you’ll need a Sysdig Secure API token.
To get your API token:
- Log in to your Sysdig Secure instance.
- Navigate to Settings > User Profile > Sysdig Secure API.
- Generate a new token or copy an existing one.
This token is required to authenticate requests from the MCP server to the Sysdig Secure backend.
Environment Variables
| Variable | Description | Example |
|---|---|---|
SYSDIG_MCP_API_HOST | Sysdig Secure API base URL | https://us2.app.sysdig.com |
SYSDIG_MCP_API_SECURE_TOKEN | API token used to authenticate to Sysdig | your-secure-token |
SYSDIG_MCP_TRANSPORT | Transport mechanism (stdio, streamable-http, sse) | stdio |
SYSDIG_MCP_MOUNT_PATH | URL prefix for HTTP/SSE deployments | /sysdig-mcp-server |
SYSDIG_MCP_LOGLEVEL | Log level (DEBUG, INFO, WARNING, ERROR) | INFO |
SYSDIG_MCP_LISTENING_PORT | Port for HTTP/SSE servers | 8080 |
SYSDIG_MCP_LISTENING_HOST | Hostname for HTTP/SSE servers | localhost |
You can set these variables in your shell or in a .env file.
Example .env file:
# Required Configuration
SYSDIG_MCP_API_HOST=https://us2.app.sysdig.com
SYSDIG_MCP_API_SECURE_TOKEN=your-api-token-here
# Optional Configuration
SYSDIG_MCP_TRANSPORT=stdio
SYSDIG_MCP_LOGLEVEL=INFO
SYSDIG_MCP_LISTENING_PORT=8080
SYSDIG_MCP_LISTENING_HOST=localhost
SYSDIG_MCP_MOUNT_PATH=/sysdig-mcp-server
API Permissions
The API token must have permissions for the tools being used.
Minimum Permissions Required
| Tool Category | Required Permissions | Sysdig UI Permission Names |
|---|---|---|
| CLI Scanner | secure.vm.cli-scanner.exec | Vulnerability Management: CLI Execution |
| Threat Detection (Events Feed) | policy-events.read | Threats: Policy Events (Read) |
| SysQL | sage.exec, risks.read | Sage: Use Sage chat (EXEC) + Risks: Access to risk feature (Read) |
Additional recommended permissions:
- Settings: API Access Token (View, Read, Edit)
Assign Permissions
To assign these permissions to a user or service account, do the following:
- Go to Settings > Access & Secrets | Roles in Sysdig Secure.
- Create a role with the permissions listed in minimum permissions required.
- Assign the role to a Service Account or user.
- Use that account’s token with the MCP server.
Service Account Limitation:
The generate_and_run_sysql tool does not currently work with Service Account tokens and will return a 500 error.
Use an API token associated with a regular user account for this tool.
Running the MCP Server
Docker Deployment (Recommended)
docker pull ghcr.io/sysdiglabs/sysdig-mcp-server:latest
docker run -e SYSDIG_MCP_API_HOST=<your_sysdig_host> \
-e SYSDIG_MCP_API_SECURE_TOKEN=<your_sysdig_secure_api_token> \
-e SYSDIG_MCP_TRANSPORT=stdio \
-p 8080:8080 \
ghcr.io/sysdiglabs/sysdig-mcp-server:latest
For HTTP/SSE Transports
docker run -e SYSDIG_MCP_TRANSPORT=streamable-http \
-e SYSDIG_MCP_API_HOST=<your_sysdig_host> \
-e SYSDIG_MCP_API_SECURE_TOKEN=<your_sysdig_secure_api_token> \
-p 8080:8080 \
ghcr.io/sysdiglabs/sysdig-mcp-server:latest
Client Configuration
Authentication
When using sse or streamable-http transport, the server expects a Bearer token in the HTTP header.
Example headers:
Authorization: Bearer <your_sysdig_secure_api_token>
X-Sysdig-Host: <your_sysdig_host>
If X-Sysdig-Host is not provided, the server uses the host from SYSDIG_MCP_API_HOST.
URL
HTTP/SSE transports:
http://<host>:<port>/sysdig-mcp-server/mcp
Example:
http://localhost:8080/sysdig-mcp-server/mcp
Claude Desktop App
To configure the Claude Desktop app manually, do the following:
- Go to Settings > Developer > Edit Config.
- Add the MCP configuration under
mcpServers:{ "mcpServers": { "sysdig-mcp-server": { "command": "docker", "args": [ "run", "-i", "--rm", "-e", "SYSDIG_MCP_API_HOST", "-e", "SYSDIG_MCP_TRANSPORT", "-e", "SYSDIG_MCP_API_SECURE_TOKEN", "ghcr.io/sysdiglabs/sysdig-mcp-server" ], "env": { "SYSDIG_MCP_API_HOST": "<your_sysdig_host>", "SYSDIG_MCP_API_SECURE_TOKEN": "<your_sysdig_secure_api_token>", "SYSDIG_MCP_TRANSPORT": "stdio" } } } } - Replace placeholders (
<your_sysdig_host>,<your_sysdig_secure_api_token>). - Save and restart Claude Desktop.
MCP Inspector
- Run MCP Inspector locally.
- Select the appropriate transport type and start your MCP server.
- Pass authentication headers (for
HTTP/SSE) or environment variables (forstdio).
Goose Agent
- Run
goose configureand follow the steps to add the Sysdig MCP extension. - Example
~/.config/goose/config.yamlsnippet:extensions: sysdig-mcp-server: cmd: sysdig-mcp-server description: Sysdig MCP server enabled: true envs: SYSDIG_MCP_TRANSPORT: stdio env_keys: - SYSDIG_MCP_API_HOST - SYSDIG_MCP_API_SECURE_TOKEN - SYSDIG_MCP_TRANSPORT timeout: 300 type: stdio
Examples and Use Cases
| Use Case | Example Description |
|---|---|
| Interactive Forensics | • List runtime security events in the last hour in cluster A. • For event ID abc123, show the full process tree. |
| Natural Language to SysQL | • List top 5 containers by CPU usage in the last 15 minutes. The MCP server converts the query to SysQL and returns results. |
| Automated Response / Playbooks | • If a cryptominer is running, open a ticket in JIRA with evidence. |
| Vulnerability Scanning (local) | • Scan image nginx:latest for vulnerabilities using the Sysdig CLI. |
| Cloud Context Enrichment | • Combine Sysdig runtime data with cloud metadata (for example, AWS tags) for context-aware remediation. |
Security Considerations
| Area | Description |
|---|---|
| Authentication & Token Management | Use short-lived or rotating tokens. Avoid embedding static credentials. |
| Input Validation & Prompt Sanitization | Guard against prompt injection attacks. Validate and sanitize client inputs before execution. |
| Least Privilege & Scope Limiting | Grant only the minimal required permissions for each use case. Avoid administrative tokens. |
| Context & Tenant Isolation | Ensure clients and tenants are isolated to prevent data leakage across contexts. |
| Audit Logging & Monitoring | Log all client requests, tool invocations, and API interactions. Monitor anomalies or abuse. |
| Tool Poisoning & Shadowing Risks | Validate tool definitions and ensure immutability to prevent tampering or stealthy changes. |
| Transport Security | Use TLS and proper token handling for HTTP transports. Never send tokens in query parameters. |
Consider adding a Threat Model section to enumerate potential threats and mitigations.