Permissions and Resources
Review Azure Roles and Permissions
Security Principals
The onboarding process involves two security principals:
- Installer: The primary security principal. This security principal will be used to perform the onboarding. Sysdig does not have access to this security principal. The Installer security principal can be either:
- A User
- A Service Principal
- Sysdig: A Service Principal (robot user) created during onboarding with specific, less permissive roles. Sysdig will be given access to this security principal.
Azure Role Types
Azure IAM is separated into two control planes:
- Entra ID Roles: Applied to the entire Tenant.
- Azure RBAC Roles: Applied to the Subscription or Management Group being onboarded.
Base Azure Integration - CSPM
Connect Azure to Sysdig to enable Cloud Security Posture Management (CSPM). CSPM assesses and manages the security posture of your cloud resources without requiring agents.
Permissions Required to Install
You must assign the Installer security principal at least the following roles:
| Role Type | Role | Description |
|---|---|---|
| Entra ID | Application Administrator | This role is required to create the Sysdig Service Principal in Entra ID. |
| Entra ID | Privileged Role Administrator | This role is required to attach Entra ID roles, such as Directory Reader to the Sysdig Service Principal. See Permissions Granted to Sysdig. |
| Azure RBAC | User Access Administrator | This role is required to attach Azure RBAC roles to the Sysdig Service Principal. To assign this role to a Service Principal Installer, see Assign User Access Administrator. To assign it to a User Installer, see Assign Roles and Permissions. |
Permissions Granted to Sysdig
The Sysdig Service Principal will be granted the following roles:
| Role Type | Role | Description |
|---|---|---|
| Entra ID | Directory Readers | Allows Sysdig to list Users and Service Principals. |
| Azure RBAC | Reader | Allows Sysdig to list resources within your Subscriptions. |
| Azure RBAC | Custom Role containing: Microsoft.Web/sites/config/list/action | Allows Sysdig to collect the AuthSettings object required by certain CSPM controls. |
Resources Created
The following resources will be created in your Azure Environment:
| Resource | Description |
|---|---|
azuread_service_principal | Service principal used by Sysdig for secure posture management |
azuread_directory_role_assignment | Assigns the “Directory Reader” role to the Sysdig Service Principal |
azurerm_role_assignment | Assigns the “Reader” role to the Sysdig Service Principal. For single subscription installations, this is applied at the Subscription level; for tenant installations, it is applied to the root Management Group. |
azurerm_role_definition | Custom role definition containing: Microsoft.Web/sites/config/list/action |
azurerm_role_assignment | Assigns the custom role to the Sysdig Service Principal |
CDR and CIEM
To enable agentless Cloud Detection and Response (CDR) and Cloud Infrastructure Entitlement Management (CIEM)/Identity Access Management (IAM), set up log ingestion. The permissions required to do this are listed below.
Permissions Required to Install
The Installer must have at least the following roles assigned:
| Role Type | Role | Description |
|---|---|---|
| Entra ID | Application Administrator | Required to create a Service Principal associated with a Sysdig-owned application. |
| Entra ID | Security Administrator | Required to create Entra ID Diagnostic Settings. |
| Azure RBAC | Owner | Required to attach Azure RBAC roles to the created Service Principal, and create Resource Groups, Event Hub resources and Diagnostic Settings. |
If you are using Service Principal to run terraform deployment please make sure to assign Contributor role to the Service principal for /providers/Microsoft.aadiam scope.
Permissions Granted to Sysdig
The Sysdig Service Principal will be granted the following roles:
| Role Type | Role | Description |
|---|---|---|
| Azure RBAC | Azure Event Hubs Data Receiver | Allows Sysdig to receive data from Event Hubs. |
Resources Created
The following resources will be created in your Azure Environment:
| Resource | Description |
|---|---|
azuread_service_principal | Service principal for Event Hub integration |
azurerm_resource_group | Resource group to contain the Event Hub and related resources |
azurerm_eventhub_namespace | Namespace for the Event Hub |
azurerm_eventhub | Event Hub for log ingestion |
azurerm_eventhub_consumer_group | Consumer group within the Event Hub |
azurerm_eventhub_namespace_authorization_rule | Authorization rule for the Event Hub namespace |
azurerm_role_assignment | Assigns the “Azure Event Hubs Data Receiver” role to the Sysdig service principal for the Event Hub namespace |
azurerm_monitor_diagnostic_setting | Diagnostic settings for the subscription |
azurerm_monitor_aad_diagnostic_setting | Diagnostic settings for Entra ID |
Vulnerability Management Agentless Host Scanning
Vulnerability Management (VM) Agentless Host Scanning performs vulnerability scanning using disk snapshots and Azure Lighthouse for accurate risk assessment and management.
Permissions Required to Install
The Installer must have at least the following roles assigned:
| Role Type | Role | Description |
|---|---|---|
| Entra ID | Application Administrator | Required to create a Service Principal associated with a Sysdig-owned application. |
| Entra ID | Privileged Role Administrator | Required to assign Entra ID roles to the created Service Principal. |
| Azure RBAC | Owner | Required to create Azure Lighthouse Definition and Assignment. |
Please make sure Microsoft.ManagedServices resource provider is registered for the specific subscription. Please follow the instructions.
Permissions Granted to Sysdig
The Sysdig Service Principal will be granted the following roles:
| Role Type | Role | Description |
|---|---|---|
| Azure RBAC | VM Scanner Operator | Allows Sysdig access to disk snapshot for security analysis. |
Resources Created
The following resources will be created in your Azure Environment:
| Resource | Description |
|---|---|
azurerm_lighthouse_definition | Defines the Azure Lighthouse relationship |
azurerm_lighthouse_assignment | Assigns the Lighthouse definition to target subscriptions |
Vulnerability Management Agentless Workload Scanning
Vulnerability Management Agentless Workload Scanning provides vulnerability scanning for Azure Functions, Azure Kubernetes Servies and Azure Container Apps.
Permissions Required to Install
The Installer must have at least the following roles assigned:
| Role Type | Role | Description |
|---|---|---|
| Entra ID | Application Administrator | Required to create the Sysdig Service Principal in Entra ID. |
| Azure RBAC | Owner or User Access Administrator | Required to create and assign custom roles to the Sysdig Service Principal. |
Permissions Granted to Sysdig
The Sysdig Service Principal will be granted the following built-in and custom roles:
| Role Type | Role | Description |
|---|---|---|
| Azure RBAC | AcrPull | Allows the service principal to pull images from the Azure Container Registry. |
| Azure RBAC | Storage File Data Privileged Reader | Grants read access to file shares. |
| Azure RBAC | Storage Blob Data Reader | Allows read access to blobs and their properties. |
| Azure RBAC | Custom Role for Azure Functions | A custom role with permissions to read function app configurations (Microsoft.Web/sites/config/list/Action, microsoft.web/sites/config/appsettings/read) and access the Kudu API (Microsoft.Web/sites/publish/Action). |
| Azure RBAC | Custom Role for AKS Discovery (Optional) | If AKS discovery is enabled, this role allows listing cluster admin credentials (Microsoft.ContainerService/managedClusters/listClusterAdminCredential/action). |
Resources Created
The following resources will be created in your Azure Environment:
| Resource | Description |
|---|---|
azuread_service_principal | A Service Principal linked to the Sysdig VM Workload Scanning application. |
azurerm_role_definition | Custom role definitions for Azure Functions and optional AKS discovery. |
azurerm_role_assignment | Assigns the required built-in and custom roles to the Sysdig Service Principal at the subscription or management group level. |
sysdig_secure_cloud_auth_account_component | Registers the Service Principal with the Sysdig backend to enable the feature. |
Assign Roles and Permissions
To apply roles in Azure, check out the Microsoft’s documentation, or use one of the Azure CLI commands given in the sections below.
After you assign a role via the Azure CLI, ensure you Reload Credentials to save your changes.
Assign User Access Administrator
To assign the role User Access Administrator to a Service Principal Installer, use the following command template:
az role assignment create --assignee "<SP_APP_ID>" --role "User Access Administrator" --scope "<ROOT_MANAGEMENT_GROUP_ID>"
Fill in the values SP_APP_ID, and ROOT_MANAGEMENT_GROUP_ID. For example:
az role assignment create --assignee "a686e05a-191d-48ba-a74e-6daf9445ef71" --role "User Access Administrator" --scope "/providers/Microsoft.Management/managementGroups/d1aed736-5b36-41ff-9d78-c8181a3435bb"
For troubleshooting, see Insufficient Permission on Tenant.
Assign Contributor Permission
To assign the role Contributor to a Service Principal Installer, use the following command template:
az role assignment create --assignee-principal-type ServicePrincipal --assignee-object-id <SP_OBJECT_ID> --scope "/providers/Microsoft.aadiam" --role Contributor
SP_OBJECT_ID: This is the Service Principal Object ID for your Enterprise Application, not the Object ID of your application. This can be found:- In the Azure Portal: Azure Active Directory > Enterprise applications > Your SP
- In the Azure CLI with the command
az ad sp show --id XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX --query id --output tsvwhere XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX is the appId of the Enterprise Application.
Example:
az ad sp show --id 21824912-8445-4a5e-b7d7-cc77c0fbxxxx --query id --output tsvOutput:
97683330-4e97-416c-9a3a-398f381exxxx
Reload Credentials
After you update RBAC roles, reload the credentials in the Azure CLI to ensure your changes are reflected.
To update credentials, run the following command in Azure CLI to update credentials:
az account clear && az login
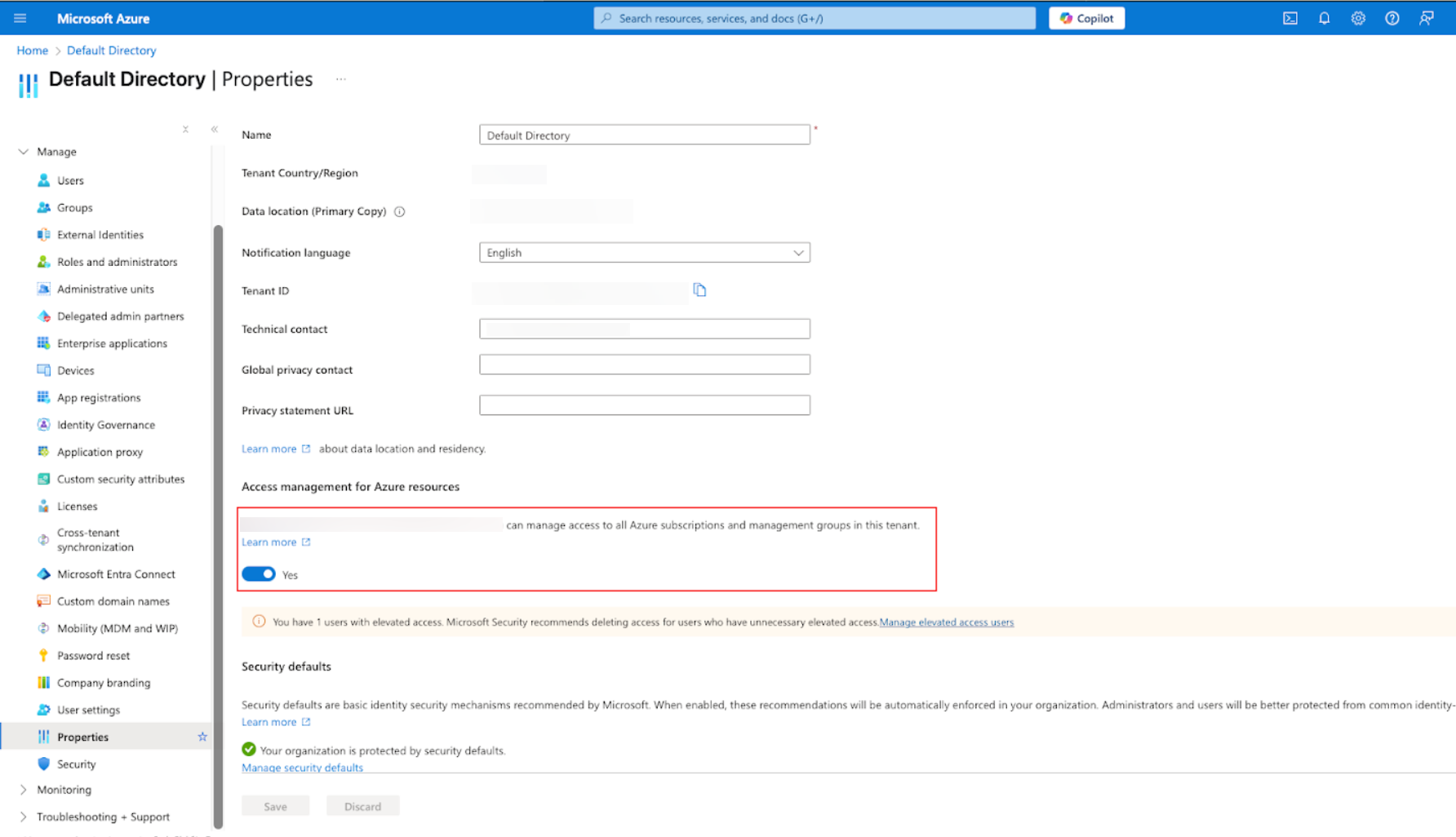
Enable Root Management Group Access
To grant Root Management Group Access (RBAC role assignment on root management group scope) to a security principal:
Go to the Microsoft Azure portal.
Navigate to Entra ID > Manage > Properties.
Under Access management for Azure resources, set the toggle to Yes.
Root Management Group Access is now enabled for the current user.