Vulnerability Admission Policies
Create and Assign Policies
To create and assign Vulnerability Policies with the Sysdig Admission Controller, you can follow the guidelines documented in the Vulnerability Management Policies documentation.
When creating a Vulnerability Admission Policy, ensure you are validating the rules and scopes in a lower environments before implementing. Do this to prevent workload disruptions in your production environments.
Vulnerability Management Events
You can observe Vulnerability Admission Control events in two places within the Sysdig Secure Platform.
- The command line interface. (CLI) where the Action was performed.
- The Events Feed.
For examples of each, see Use Cases and Examples.
Reject and Scan Actions
When using the Reject and Scan action, the Admission Controller performs scans on a best-effort basis. Results appear with the associated Rejection and subsequent events the Events Feed after some time.
We recommend you scan your images in your CI/CD Pipelines and Registries before they are deployed.
Use Cases and Examples
The following are a few examples of Admission Controller use cases and guidance on how you can use the Sysdig Admission Controller to enforce your organizational best-practices.
Reject Images with Critical Vulnerabilities with Exploits Available
By using the Severities and Threats Rule type defined in the Vulnerability, Image Configuration and Content, you can define the following rule to ensure no Critical Vulnerabilities with Exploit Criteria reach your runtime environments:
- Create a Rule Bundle with the following Vulnerability, Image Configuration and Content enabled:
Severities and Threats- With
SeverityGreater than or EqualsCritical - Exploitability Metrics
- Public Exploit Available
- With
- Create a Vulnerability Management Policy and attach the previously created Rule Bundle.
- Set the Admission Control Stage with the scope set to
All Infrastructure - Set the Policy Action to
Reject
- Set the Admission Control Stage with the scope set to
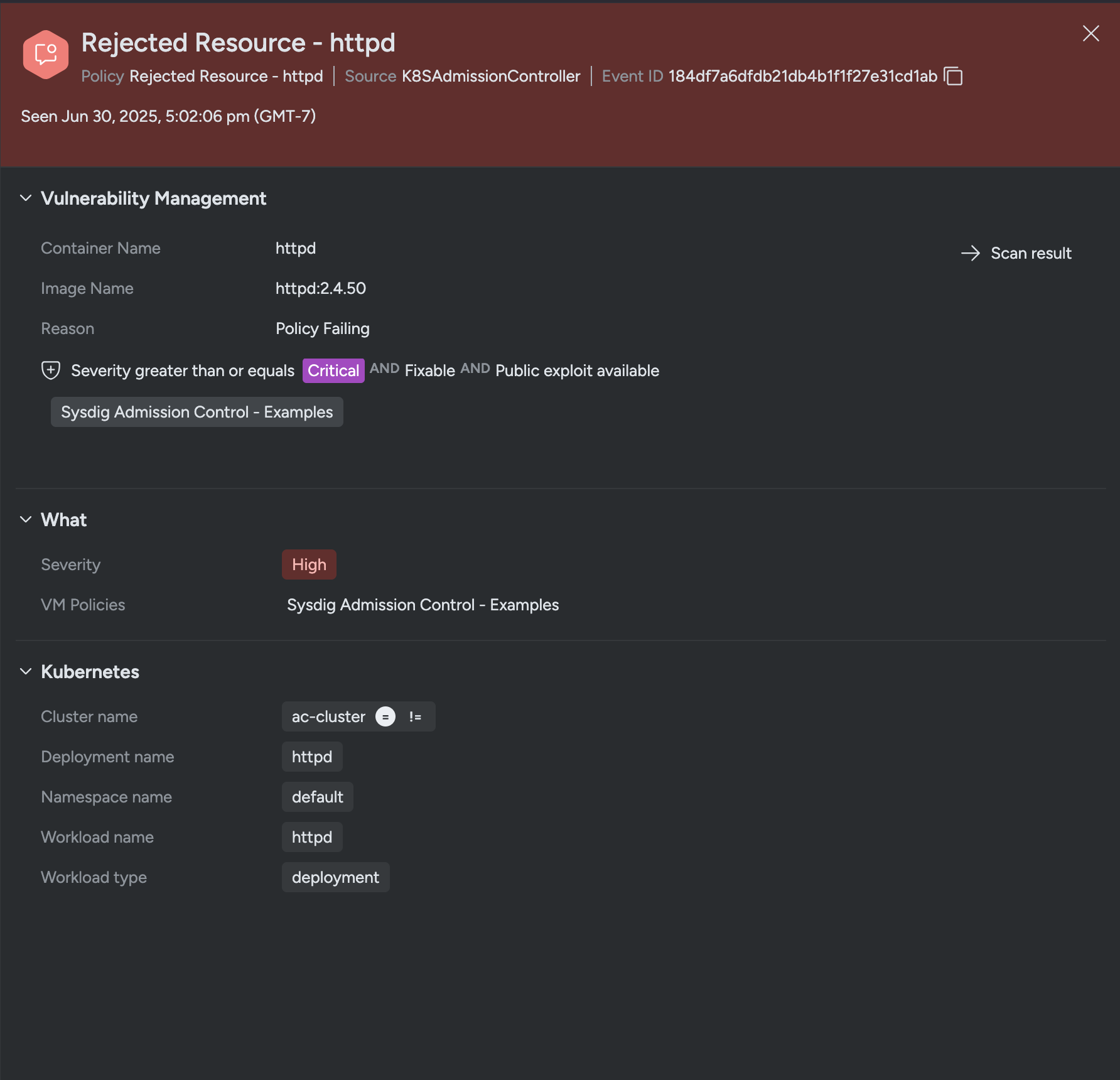
Once saved you can test the Policy Action by deploying a known bad workload and observing the failures in the CLI during kubectl execution and Events Feed
CLI
kubectl create deployment httpd --image=httpd:2.4.50
error: failed to create deployment: admission webhook "vac.secure.sysdig.com" denied the request:
[VM Engine] Failed checks for container httpd. Failing policies: [Sysdig Admission Control - Examples]
Violations:
x Fixable
x Public Exploit available
x Severity greater than or equal critical
Events Feed
Reject Unknown Images and Implement Deploy-Time Image Scanning (Unscanned Images)
By implementing the Reject and Scan functionality on Unknown Images, you can prevent unknown Third Party images from entering your cluster or Images that may not have been scanned in a previous stage such as CLI or Pipeline.
Similar to above, implement a Policy with a pre-defined Rule Bundle and when selecting the
Admission Controlstage set the following in your Admission Controller Stage:- Unknown Image Actions:
Reject and Scan
This will allow you on-top of your already defined Rule Bundles, prevent Unknown Images from entering your clusters.
- Unknown Image Actions:
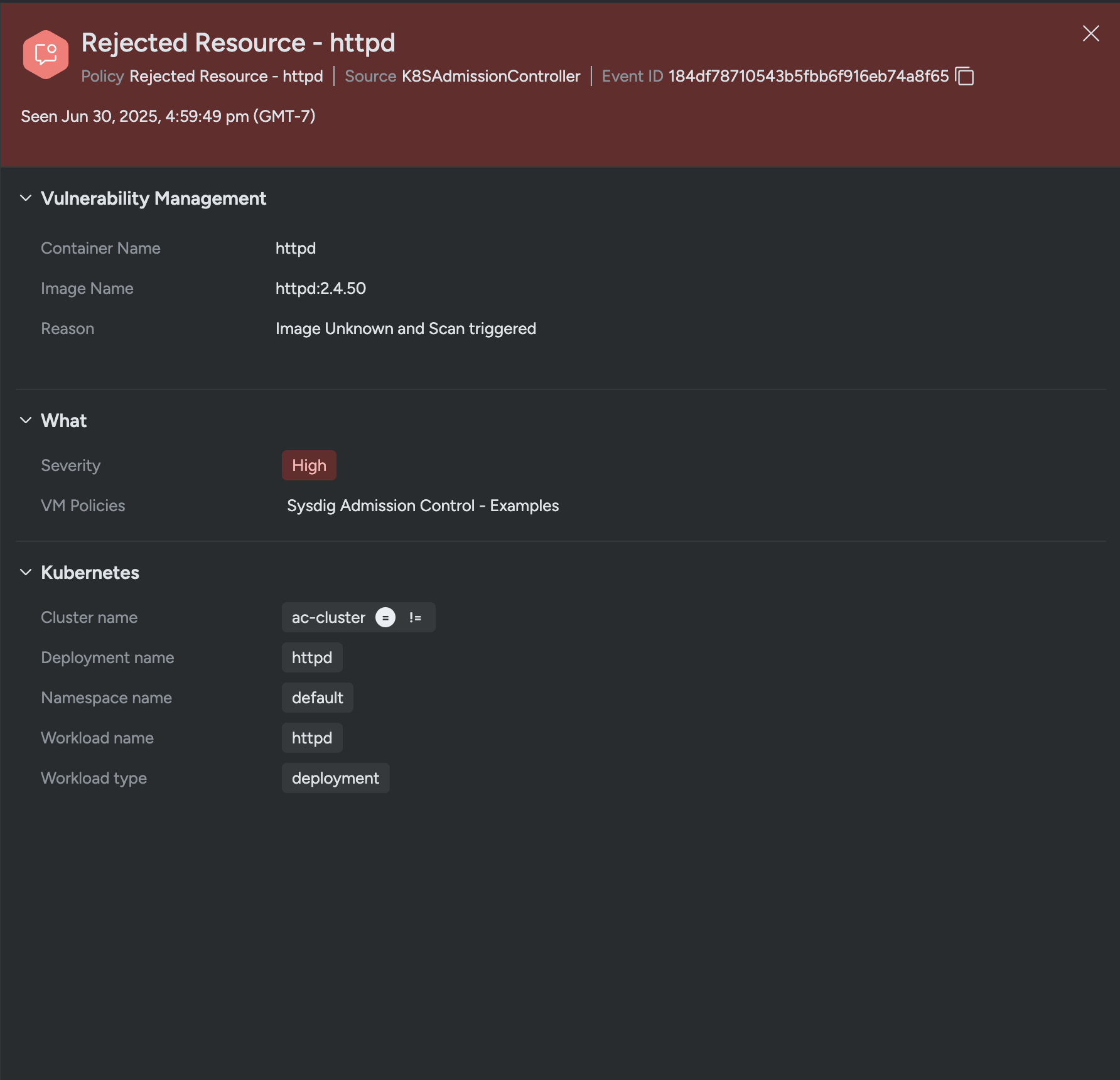
You can view these events in the CLI during
kubectlexecution or in the Events Feed.
CLI
kubectl create deployment httpd --image=httpd:2.4.50
error: failed to create deployment: admission webhook "vac.secure.sysdig.com" denied the request:
[VM Engine] Failed checks for container httpd, image is not known. Failing policies: [Sysdig Admission Control - Examples]
Events Feed
Scans performed by the Admission Controller are performed on a Best Effort basis and will appear in the Event after some time. It is always recommended to pre-scan your images in your CI/CD Pipelines and Registries before they are deployed.
Enforce specific Image Labels for Image Ownership
By using the Image Configuration Rule type defined in the Vulnerability, Image Configuration and Content you can define the following rule to ensure your development teams are appropriately tagging their images before they reach your runtime environments.
- Create a Rule Bundle with the following Vulnerability, Image Configuration and Content enabled
Image Label- Label
org.opencontainers.image.authorsdoes not exist and value does not contain@example.com
- Label
- Create and add this Rule to a Vulnerability Management Policy
- Set the Admission Control Stage with the scope set to
All Infrastructure - Set the Policy Action to
Reject.
- Set the Admission Control Stage with the scope set to
- Save your changes.
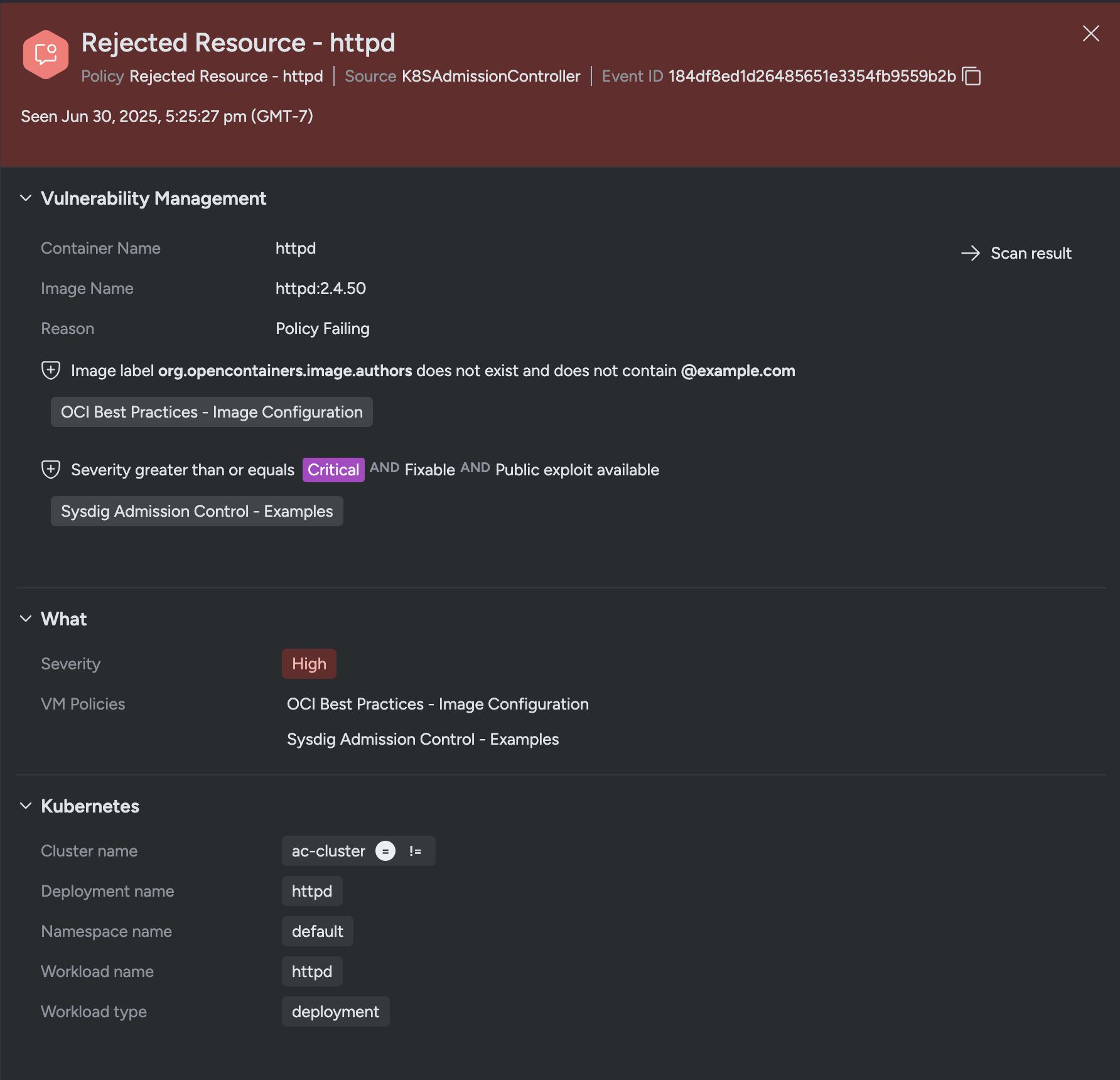
- To test the Policy Action, deploy a known bad workload and observe the failures in the CLI or the Events Feed during
kubectlexecution.
CLI
kubectl create deployment httpd --image=httpd:2.4.50
error: failed to create deployment: admission webhook "vac.secure.sysdig.com" denied the request:
[VM Engine] Failed checks for container httpd. Failing policies: [OCI Best Practices - Image Configuration, Sysdig Admission Control - Examples]
Violations:
x Fixable
x Public Exploit available
x Severity greater than or equal critical
x Value @example.com not found in label org.opencontainers.image.authors