Manage Vulnerability Exceptions and Global Lists
End of Life Notice: The Sysdig Legacy Scanning Engine will reach its End of Life (EOL) on December 31st, 2024. After this date, it will no longer be supported or maintained. Please upgrade to our New Scanning Engine before December 31st, 2024 to ensure continuous service and support. For assistance, contact our support team or your account representative.
Sysdig Secure allows users to add specific CVEs to Global Exception lists. Common reasons to exempt a vulnerability from consideration while scanning an image include, for example:
Knowing that the vuln does not apply to your runtime or cannot be exploited
Knowing that the suggested “fix version” will break a chain of dependencies, and you plan to evaluate how to patch this vulnerability in more detail
Knowing that there is no available fix for the vulnerability yet and you absolutely must deploy this application in production. (You decide to use a temporary alternate security strategy to protect from the vulnerability.)
When devising exception lists, you can detail what exceptions you introduce, for which images, and for how long, establishing a vulnerability exception management workflow.
Additionally, specific images can be marked as untrusted or globally trusted to ensure they always/never pass a scan.
Previous versions of Sysdig Secure called this feature Whitelist and Blacklist, and the options were located under the Scanning Policies tab.
Create Multiple Exception Lists
By default, a single list is provided. Its name,
Default exceptions list, can be retitled or removed if desired.
To create additional lists:
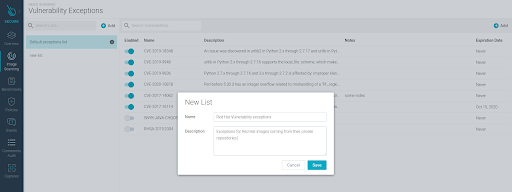
Select
Image Scanning > Vulnerability Exceptionsand click theAddbutton on the left side of the screen.Enter a
NameandDescriptionand clickSave.Hover over the info bubble on an existing list to see its name, description, and last-modified date.
For an exception list to be applied to an image during a scan, you must set up a scanning policy assignment to map the image to the list.
If you delete or rename an exception list, the modification will be also applied to the policy assignments that contain that list.
Add a Vulnerability to a List
There are two ways to add a vulnerability to a list: from the Exceptions List page, or from the Scan Results.
From the Exceptions List Page
Select
Image Scanning > Vulnerability Exceptionsand choose the desired list from the left menu. (In this example, the Exception list is named “Python exceptions”.)Click the
Addbutton on the right side of the screen.Enter the identifying details:
CVE ID: Required
Expiration Date: Required, but can be ’never'
Note Optional.
From the Scan Results
The scan results for an image may flag vulnerabilities you don’t consider necessary. From the results list, you can quickly append those entries to exception lists as follows:
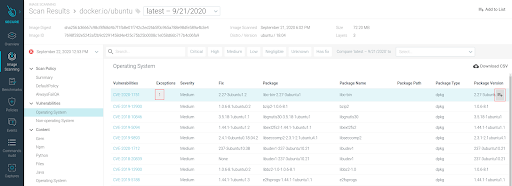
Select
Image Scanning > Scan Results.Select the Vulnerability type from the left menu and review the resulting list of flagged vulnerabilities.
Note: The
Exceptionscolumn displays the number of lists already containing this vulnerability.Click the hover button to open the “Add Exception” dialog .
Enter the details and click
Save.List: Sysdig will indicate with a “radar” icon the lists that are being applied to this image according to the policy assignments which are relevant for the evaluation of this particular image
You can also enter additional list names in the field to create a new list.
Expiration Date: Required, but can be ’never'
Note Optional.
Manage Vulnerabilities in a List
An exception list can contain any number of vulnerabilities. Each vulnerability listing displays additional properties to help the security team understand the context, feed sources, and the justification and time span for the vulnerability to be on the list.
Fields in the List View
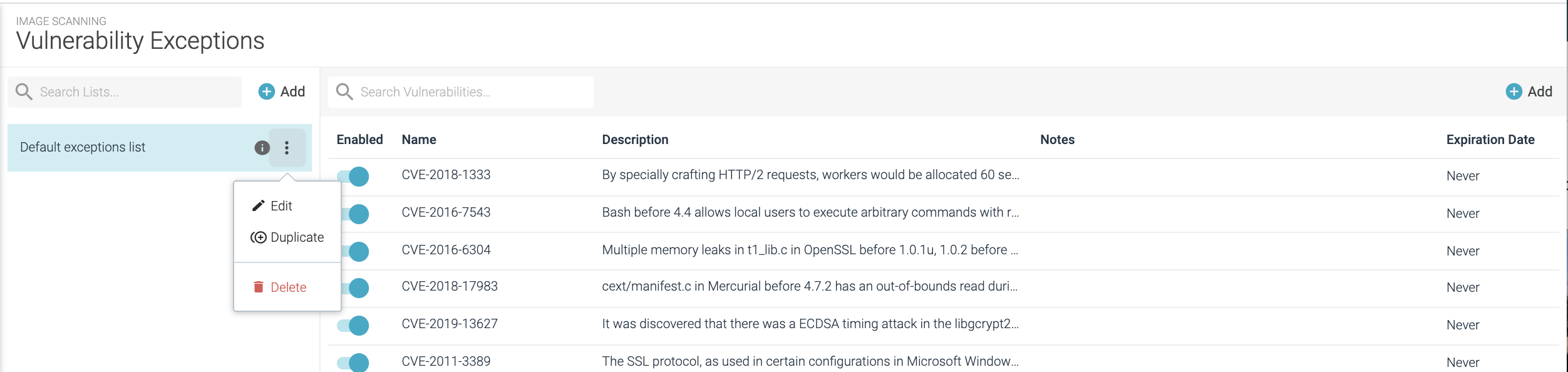
Select Image Scanning > Vulnerability Exceptions and choose a list from the left menu to review the vulnerability list details.
Review the column data:
Enabled: On/off toggle for whether the exception for this vulnerability is active. If the vulnerability exception is disabled, it will not disappear from the list but will not be taken into account when evaluating an image. Rows that have met their expiration date are automatically disabled.
Name: String entered by the user to identify the vulnerability. For example,
CVE-2019-9639orVULNDB-213986.Description: Vulnerability description, provided by Sysdig once the Vuln ID is provided by the user.
Notes: User-defined exception notes. Could be used to justify the decision or to append any additional links or information.
Expiration date: Day configured by the user for this exception to expire.
Default is
never, for a vulnerability that should not expire. If an expiration is set, thendayis the minimum time resolution.All expiration dates are evaluated against 0:00 UTC timezone
Access and Edit Additional Details
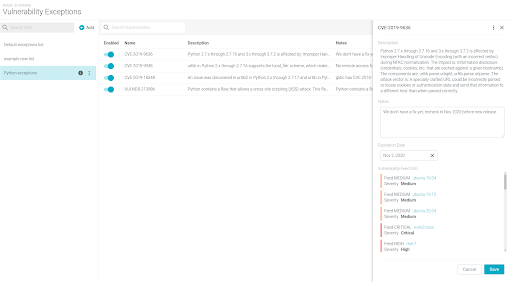
Click on an exception row to see additional details about the vulnerability and to edit its properties.
You can:
View the full description
View and modify user notes
View and modify Expiration date
Disabled exceptions cannot be re-enabled until a future date is set.
View segmented feed information, for every feed that is reporting this vulnerability:
Severity of the vulnerability as reported per each individual feed (color-coded)
Link to vulnerability details as provided per feed
Add Images to a Global List
There are two ways to add images to a Global Trusted or Untrusted list: from the list or from a scan result.
From the Global list:
From the
Image Scanningmodule, select eitherGlobal - Trusted ImagesorGlobal - Untrusted Images.The list of previously added images is displayed.
Click the
Add Imagebutton.Add each image in a comma-separated list, then click
Ok.A tag name must be valid ASCII and may contain lowercase and uppercase letters, digits, underscores, periods and dashes.
A tag name may not start with a period or a dash and may contain a maximum of 128 characters.
From the Scan Results:
From the
Image Scanningmodule, choose theScan Resultstab.Select the relevant repository from the list and open the relevant image.
Click
Add to Listat the top of the page.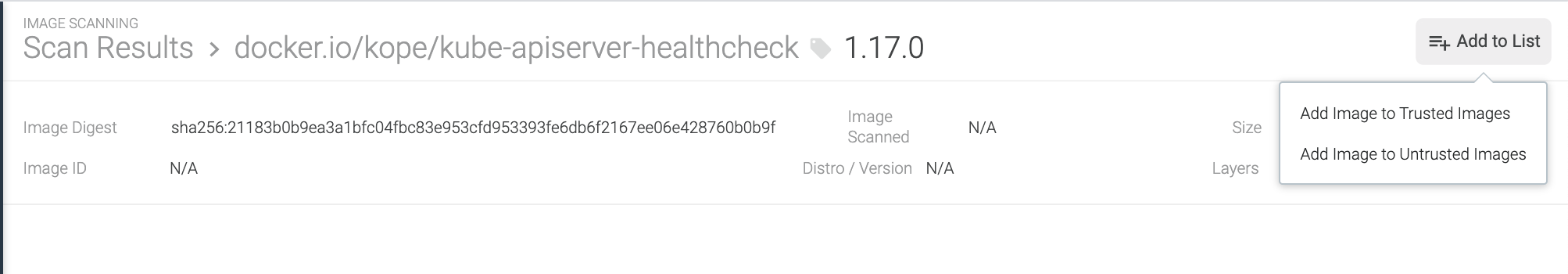
Select either
Add Image to Trusted ImagesorAdd Image to Untrusted Imagesas needed.