Cloud Run Service (Controlled Availability)
Cloud Run Service is currently in Controlled Availability. Contact Sysdig representative to enable this feature.
You can install the Sysdig Serverless Workload Agent on an instance to provide security. It requires network access to communicate with the Sysdig Collector.
It monitors the workload container(s) and enforces the Falco rules to detect security threats.
Prerequisites
Refer to the following prerequisites for both Sysdig and GCP Cloud Run.
- Review the Installation Requirements before getting started.
Sysdig Side
Your agent access key
Find the Sysdig collector endpoint for your region. See SaaS Regions and IP Ranges.
Retrieve your Agent Access Key.
GCP Cloud Run Side
Instance-based billing (previously called CPU Always Allocated) selected in your Service definition.
Second-generation execution environment selected in your Service definition.
Deploy the Sysdig Workload Agent
The Serverless Workload Agent is composed of two main components bundled together in a docker image:
- An instrumentation application that monitors the workload container.
- An agent that collects security events from the instrumentation application and communicates with the Sysdig backend.
You can deploy the Sysdig Workload Agent in two ways:
- In the ingress container: In this mode both the instrumentation application and the agent run in the ingress container.
- As a sidecar: In this mode the instrumentation application runs in the ingress container and the agent runs as a sidecar.
The sidecar deployment allows setting a dedicated memory and CPU allocation for the agent.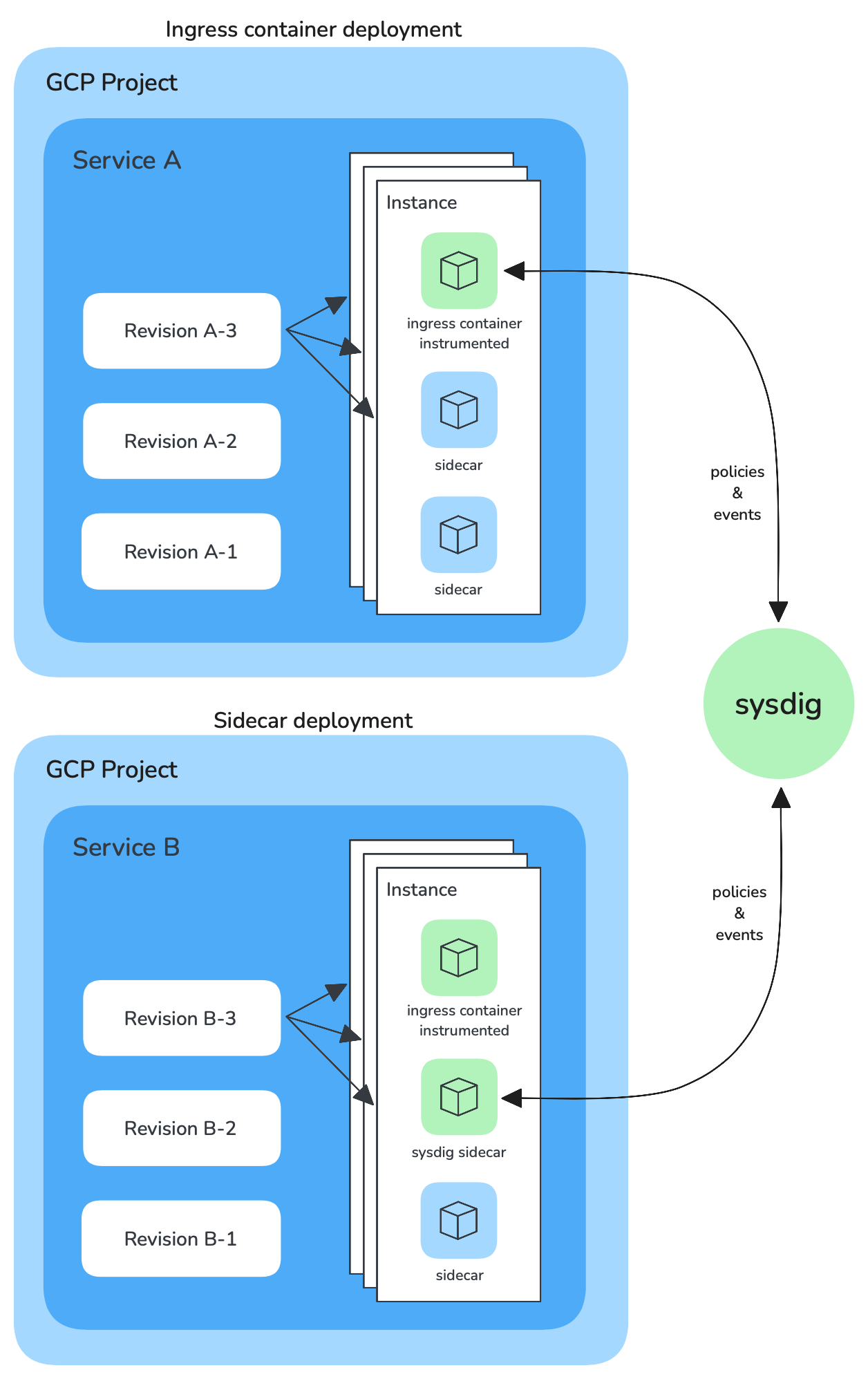
Deploy in the Ingress Container
To instrument your ingress container at build time, include the Sysdig Workload Agent in a container image, and then deploy the resulting image to Cloud Run.
- Update your Dockerfile to copy the required files and specify the required environment variables.
Consider the following example image:
FROM falcosecurity/event-generator:latest
ENTRYPOINT ["/bin/event-generator"]
CMD ["run", "syscall", "--all", "--loop"]
- Modify the image as follows:
ARG SYSDIG_AGENT_VERSION=latest
FROM quay.io/sysdig/workload-agent:${SYSDIG_AGENT_VERSION} AS workload-agent
FROM falcosecurity/event-generator:latest
COPY --from=workload-agent /opt/draios /opt/draios
ENTRYPOINT ["/opt/draios/bin/instrument"]
CMD ["/bin/event-generator", "run", "syscall", "--all", "--loop"]
- Include the Workload Agent in the final layer of your image by updating the Dockerfile.
ARG: Specifies the version of the Sysdig Workload Agent to use, which defaults to the latest version if not specified.FROM: Pulls the Sysdig Workload Agent image.COPY: Use theCOPYcommand to copy the/opt/draiosdirectory from the Sysdig Workload Agent image into your container image.
Modify the
ENTRYPOINTof your image to be/opt/draios/bin/instrumentand prepend the original entrypoint to theCMD.Build and push the container image to your container registry.
Deploy the container image to Cloud Run Service as you would with any other container image, and provide it with the following additional environment variables:
SYSDIG_COLLECTOR: The endpoint of the Sysdig Collector.SYSDIG_COLLECTOR_PORT: The port of the Sysdig Collector. The default is 6443.SYSDIG_ACCESS_KEY: The access key to authenticate with the Sysdig backend.SYSDIG_WORKLOAD_ID: The unique alphanumeric identifier for the agent at the service level.
Deploy in Sidecar
Instrument your docker image at build time, as described in deploying ingress container.
Add a sidecar container to the service running the Sysdig Workload Agent.
The ingress container (instrumented at build time) requires the following environment variable:
SYSDIG_SIDECAR:force
The Sysdig Workload Agent sidecar container requires the following environment variables:
SYSDIG_COLLECTOR: The endpoint of the Sysdig Collector.SYSDIG_COLLECTOR_PORT: The port of the Sysdig Collector, 6443 as default.SYSDIG_ACCESS_KEY: The access key to authenticate with the Sysdig backend.SYSDIG_WORKLOAD_ID: The workload ID, a unique identifier for the workload.SYSDIG_SIDECAR:force
spec:
containers:
- name: ingress-container
...
- name: sysdig-agent
image: quay.io/sysdig/workload-agent:latest
env:
- name: SYSDIG_COLLECTOR
value: collector.sysdigcloud.com
- name: SYSDIG_COLLECTOR_PORT
value: '6443'
- name: SYSDIG_WORKLOAD_ID
value: my_unique_id
- name: SYSDIG_ACCESS_KEY
value: my_access_key
- name: SYSDIG_SIDECAR
value: force
- Add an in-memory volume to the service and mount it in both the ingress and the sidecar container under the path
/opt/draios/run.
spec:
...
volumes:
- name: sysdig
emptyDir:
medium: Memory
sizeLimit: 512Mi
containers:
- name: ingress-container
...
volumeMounts:
- name: sysdig
mountPath: /opt/draios/run
- name: sysdig-agent
...
volumeMounts:
- name: sysdig
mountPath: /opt/draios/run
Feedback
Was this page helpful?
Glad to hear it! Please tell us how we can improve.
Sorry to hear that. Please tell us how we can improve.