Users
Deprecation Notice
Upcoming Changes to Sysdig Product Line
The legacy Identity pages are now deprecated and will be phased out over a transition period. During this time, both the legacy and new experiences will remain available. We encourage you to start using the new Identity Overview and Findings pages to become familiar with the updated experience.
Filter and Sort Accounts
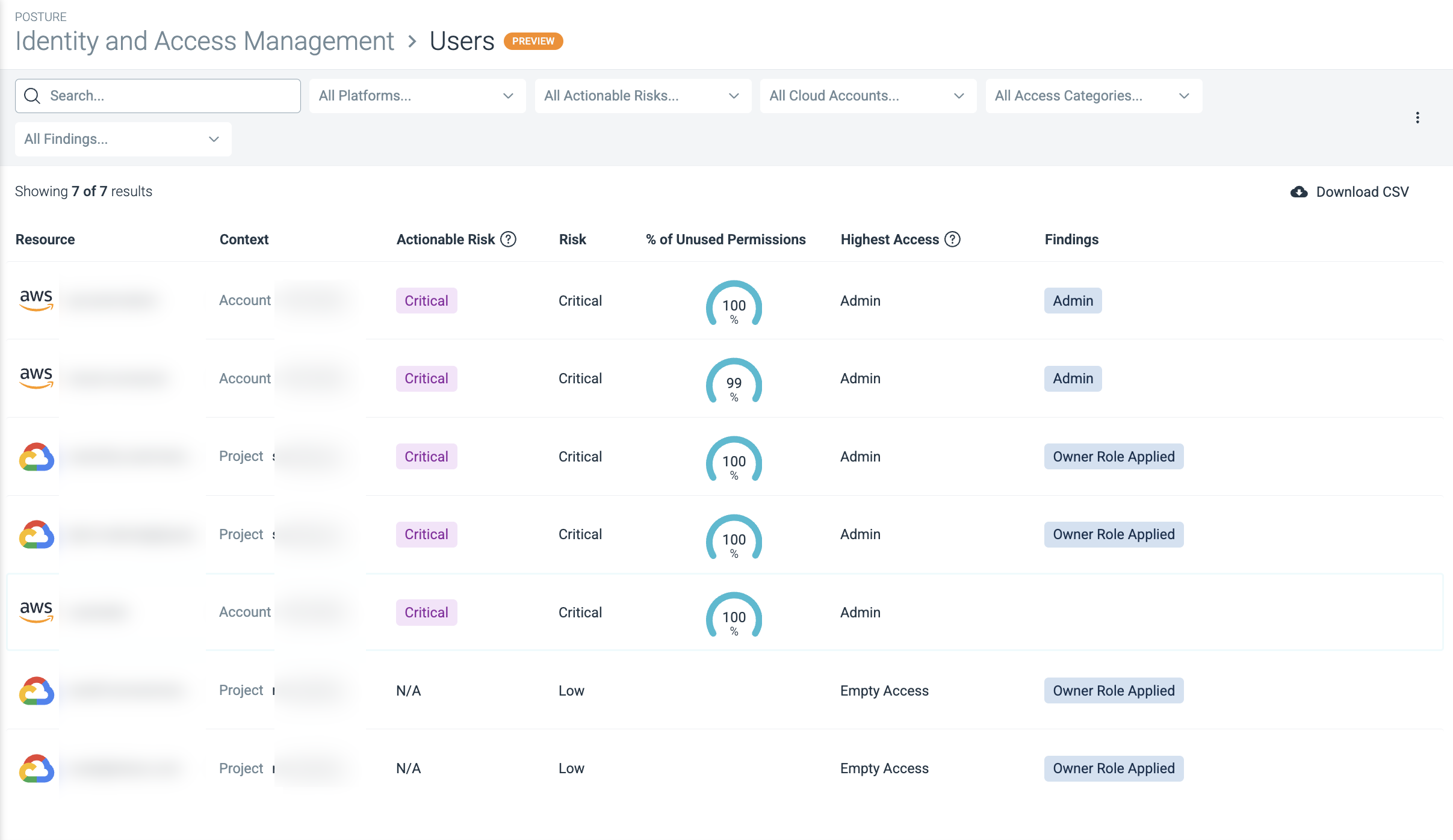
Use the sortable columns to organize and filter user accounts for assessing identity risks. You can sort user accounts based on the following criteria:
Unused Permission Criticality
Unused Permission Criticality focuses on unused permissions, while Permission Criticality looks at all permissions. Unused Permission Criticality is designed to help you achieve Least Permissive access.
Values: Critical, High, Medium, Low
Risk
This is a calculation of risk based on all permissions. See Understanding Risk Scoring for more information.
Values: Critical, High, Medium, Low
% of Unused Permissions
This shows the number of unused permissions per total permissions for the user, shown as a percentage graph.
When remediating, immediately target the users with the greatest exposure and refine them according to the suggestions.
Highest Access
Highest Access offers a quick way to filter by Access Category. It shows this identity entity’s highest level of access according to all of its permissions. For more information, see Understand Highest Access.
Values:
- Admin: Admin access granted
- Write: Write access granted
- Read: Read access granted
- Empty Access: No permissions are granted at all
Findings
A finding in Cloud Infrastructure Entitlement Management (CIEM) indicates poor security hygiene, either due to misconfiguration or inadequate identity security practices. The findings on User pages include:
No MFAAdmin
AWS-Specific
Access Key Not RotatedMultiple Access Keys ActiveRoot UserInactive
GCP-Specific
Editor Role AppliedOwner Role Applied
Available Filters
- Search: Free text search on terms in the resource name
- Unused Permission Criticality: By severity
- Cloud Accounts: Account name or account number by cloud provider. For example,
AWS - Access Categories:
Admin,Write,Read, orEmpty Access - Policy Types:
AWS-Managed,Customer,Inline - Findings: See Findings
Next Steps
To reduce the entitlements for a particular user, click on the user name to open the detail drawer and subtabs.