GCP
Prerequisites
Installed Applications
Sysdig Secure SaaS with
administratorpermissionsTerraform must be installed on the machine from which you will deploy the installation code, along with:
Terraform Google Platform Provider
Google’s Cloud software development kit (SDK) must be deployed in the environment where you will deploy the installation code.
For further guidance, see the Hashicorp and Google documentation: Install Terraform; Google Platform Provider; Install the gcloud CLI.
Have on hand:
- For Organizations: The GCP Organization domain, Organization Member Project ID, and Region
- For Projects: The Project ID
Review GCP Roles and Permissions
Review these concepts before preparing your environment and running the onboarding wizard. To assign user roles, enable APIs, and configure domain-wide delegation, you will need to log in to and access two different GCP consoles at different times:
Review the permissions allotted to the Sysdig service account through domain-wide delegation.
User Types
If you install by hand or on your local machine, you will want likely to install as a user. If you are automating the installation, such as using Terraform Cloud, you will likely want to install as a service account.
You can:
- Use an existing user or service account that meets the permissions requirements
- Create a new user or service account and set up permissions
- Add permissions to an existing user or service account
Permissions Required to Install
Single Project
The installing user/service account must have the following roles assigned on the Project that is being onboarded:
roles/iam.serviceAccountAdminroles/iam.roleAdminroles/resourcemanager.projectIamAdminroles/iam.serviceAccountKeyAdmin
If you are installing CDR, you must have the following additional roles assigned on the Project that is being onboarded:
roles/pubsub.adminroles/logging.configWriterroles/iam.serviceAccountUser
Organization
Note: Certain roles are required at the organization level. Other roles are required on a single project in which you will deploy shared resources. Ensure you have the correct roles assigned at the correct scope.
The installing user/service account must have the following roles assigned:
roles/iam.serviceAccountAdmin(On the project where shared resources will be created)roles/iam.organizationRoleAdmin(At the Organization level)roles/resourcemanager.organizationAdmin(At the Organization level)roles/iam.serviceAccountKeyAdmin(On the project where shared resources will be created)
If you are installing CDR, you must have the following additional roles assigned:
roles/pubsub.admin(On the project where shared resources will be created)roles/logging.configWriter(On the project where shared resources will be created)roles/iam.serviceAccountUser(On the project where shared resources will be created)
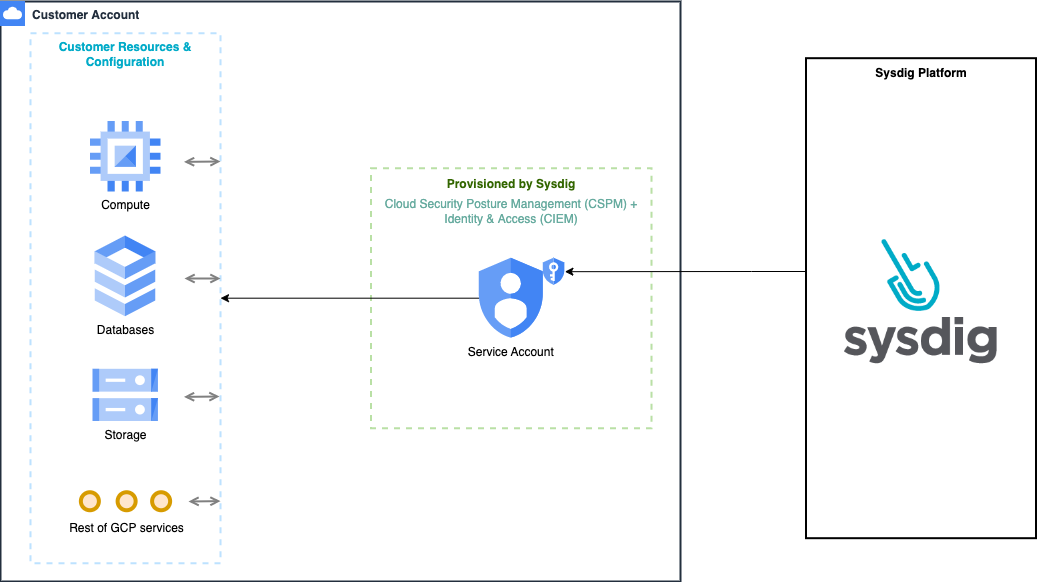
Permissions Granted to Sysdig
The installation also creates a service account that Sysdig can access. This service account will be granted the following roles:
roles/browserroles/cloudasset.viewerroles/logging.viewerroles/recommender.viewerroles/container.clusterViewerroles/compute.viewerroles/iam.serviceAccountTokenCreatorroles/iam.serviceAccountViewerroles/iam.roleViewerroles/roles/cloudfunctions.viewerin order to retrieve all cloud functions within the projectroles/cloudbuild.builds.viewerin order to retrieve the last cloud build of every existing cloud function
If Vulnerability Host Scanning is Added
roles/iam.workloadIdentityUserpermissions/iam.servieAccounts.getAccessTokenpermissions/compute.zoneOperation.getpermissions/compute.disk.listpermissions/compute.disk.getpermissions/compute.disk.useReadOnlypermissions/compute.instance.listpermissions/compute.instance.getpermissions/compute.instance.network.listpermissions/compute.instance.network.get
Prepare Your Environment
Preparation of your GCP environment, roles, and permissions is the key to a seamless connection between your GCP cloud accounts and Sysdig. When preparation is complete, the installation itself is a simple, wizard-guided process from the Sysdig Secure UI.
Follow each of the steps below to prepare for onboarding.
Step 1: Provide User with Appropriate Roles
Ensure your user has the correct roles and permissions in GCP to perform the onboarding.
Single Project
To check or assign roles:
- Log in to the Google Cloud Console as either a user or a service account, ensuring you have the correct project active.
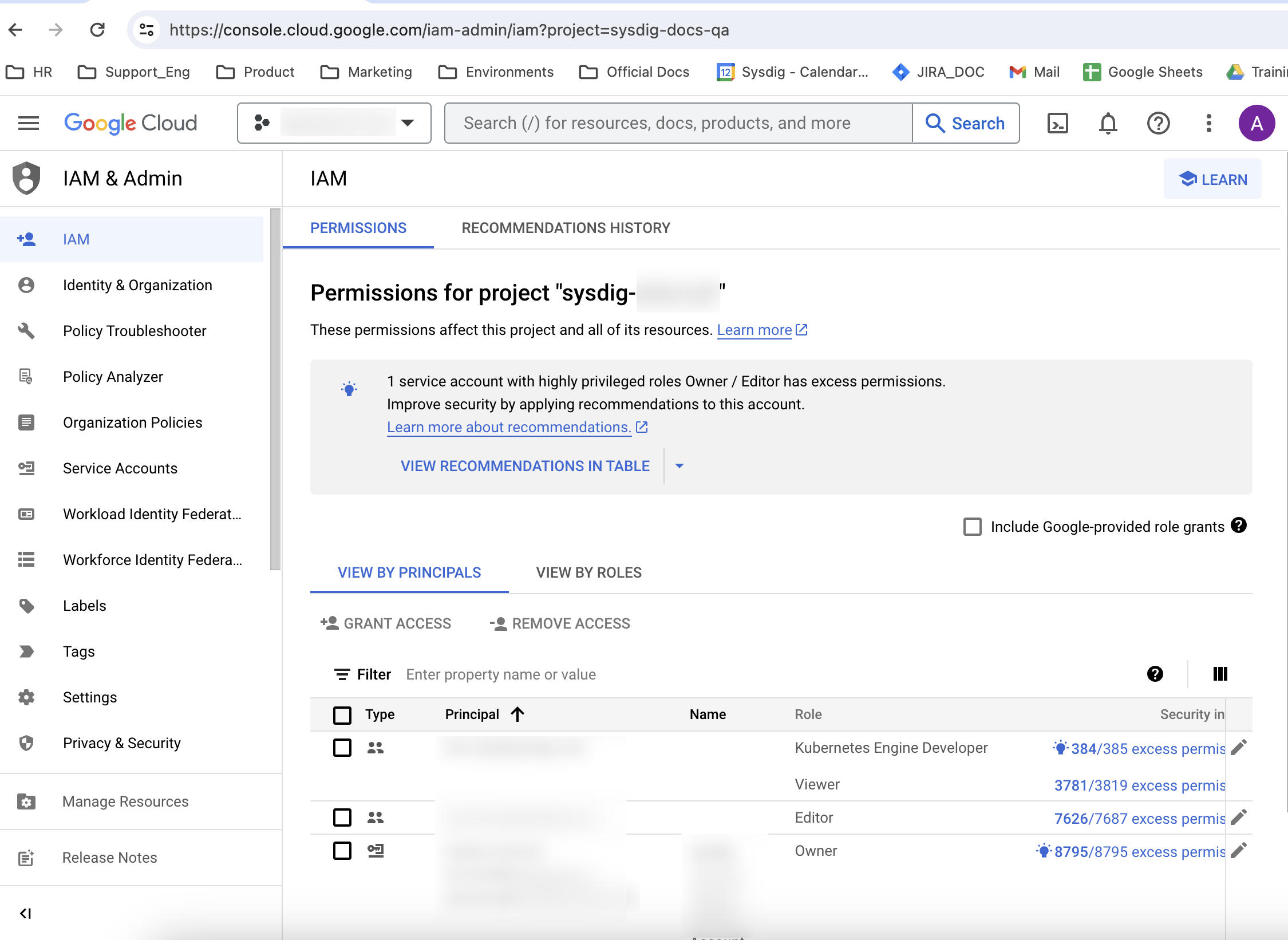
- Navigate to IAM & Admin > IAM.
- In VIEW BY PRINCIPALS, find your User/service account.
- Ensure that all the roles listed in Permissions Required to Install are present.
- If any roles are missing, select your user/service account, and grant the roles using the Grant Access button. You may need to work with your administrator to be granted the correct roles.
Organization
NOTE: Certain roles are required at the organization level. Certain roles are required on a single project in which you will deploy shared resources. Ensure you have the correct roles assigned at the correct scope.
For roles required on a single project, follow the instructions for a single project above.
For roles that are required at the organization level:
- Log in to the Google Cloud Console as either a user or a service account.
- Ensure the organization is selected in the project selector in the top bar. If you do not see your organization there, you may need to work with your administrator.
- In VIEW BY PRINCIPALS, find your User/Super Administrator.
- Ensure that all the roles listed in Permissions Required to Install are present.
- If any roles are missing, select your user/service account, and grant the roles using the Grant Access button. You may need to work with your administrator to be granted the correct roles.
Step 2: Enable Required APIs
The APIs must be enabled at the project level.
To do so manually:
| API Name | Used For | Which Project(s) |
|---|---|---|
Identity and access management API (iam.googleapis.com) | All | All |
IAM Service Account Credentials API (iamcredentials.googleapis.com) | All | All |
Cloud Resource Manager API (cloudresourcemanager.googleapis.com) | All | All |
Security Token Service API (sts.googleapis.com) | CSPM/CIEM | All |
Recommender API (recommender.googleapis.com) | CSPM/CIEM | All |
Cloud Identity API (cloudidentity.googleapis.com) | CSPM/CIEM | All |
Admin SDK API (admin.googleapis.com) | CSPM/CIEM | All |
Cloud Asset API (cloudasset.googleapis.com) | CSPM/CIEM | All |
Cloud Pub/Sub API (pubsub.googleapis.com) | CDR | Project containing shared resources |
Check API Enablement
To confirm that the required APIs were enabled:
Enable the
serviceusage.googleapis.comService API.This is required to execute the following command.
Execute:
gcloud services list --enabled
All the services listed above should be included.
Step 3: Authenticate and Configure Terraform
Configure your environment from your local machine, preparing to apply Terraform.
Ensure the prerequisites are met:
- Terraform v.1.3.1+ installed
- gcloud CLI installed
Authenticate your user and configure Terraform to use these credentials.
A common way to do this is:
Ensure you are logged in to the correct project.
Log in using the GCP CLI:
gcloud auth application-default loginYou will be presented with a web page to select your user account. Be sure to log in as the user you configured in Step 1.
Confirm you are logged in as the correct user, by running the following and confirming that the expected user is active:
gcloud auth list
For assistance, or instructions on alternative ways to authenticate Terraform, see the Terraform documentation: Google Provider Configuration Reference.
Install using Wizard
Ensure you are authenticated to the GCP project you want to connect to in your terminal window. You can authenticate using the GCP CLI by running:
gcloud auth application-default login.Log in to Sysdig Secure as
admin, select Integrations|Cloud Accounts > GCP, and select +Add GCP Account.It is possible to install agentless CDR only.
In all other cases, all agentless AWS installations include CSPM.
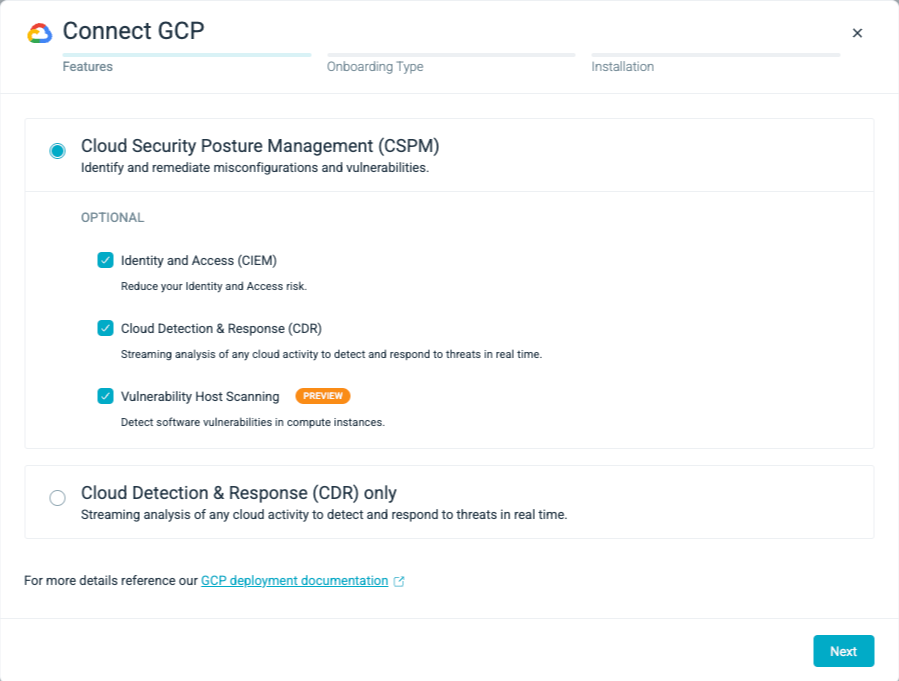
All features are included by default. Deselect individual features if desired:Identity and Access (CIEM)
Cloud Detection and Response (CDR)
Vulnerability Host Scanning
and click Next.
Select which installation method matches your enterprise and click Next.
- Organization: Configure GCP for an Organization
- Project: Configure GCP for a single Project
The Installation screen appears.
Installation
The entries on this page differ slightly depending on whether it’s an Organization or Project installation.
Organization
As prompted by the wizard screen, specify the following:
- Organization Domain: The domain of the GCP organization you are onboarding.
- Region of your GCP Project: The region where resources will be created in your GCP project.
- Project ID: The GCP project where the Sysdig resources will be deployed.
The wizard will auto-populate a code snippet, along with autodetected Sysdig Secure endpoint and Sysdig Secure API token information.
Create a file called
main.tf.Copy the code snippet from the Wizard into the file and run
terraform init && terraform apply.(CSPM+CIEM only): Click Next in the wizard to set up Domain-Wide Delegation in the Google Cloud Admin Console. Enabling DWD is optional and can be omitted if you don’t want to provide those permissions to Sysdig.
After deploying, validate the services are working.
Project
As prompted by the wizard screen, specify the following:
- Region of your GCP Project: The region where resources will be created in your GCP project.
- Project ID: The ID of the GCP project that you are onboarding.
The wizard will auto-populate a code snippet, along with autodetected Sysdig Secure endpoint and Sysdig Secure API token information.
Create a file called
main.tf.Copy the code snippet from the Wizard into the file and run
terraform init && terraform apply.(CSPM+CIEM only): Click Next in the wizard to set up Domain-Wide Delegation in the Google Cloud Admin Console. Enabling DWD is optional and can be omitted if you don’t want to provide those permissions to Sysdig.
Configure domain-wide delegation.
It allows a Google Workspace super admin to delegate authority to Sysdig service account to access user data on behalf of users within the domain.
After deploying, validate the services are working.
Configure Domain-Wide Delegation
What Is Domain-Wide-Delegation
In GCP, domain-wide delegation (DWD) refers to a feature in Google Workspace (formerly G Suite). It allows a Google Workspace super admin to delegate authority to a service account to access user data on behalf of users within the domain. Once set up, Sysdig uses a service account that can impersonate users by specifying the subject parameter in its authentication request, setting it to the email address of the Google Workspace user it wishes to impersonate.
Domain-wide delegation entails:
- Service Account Access: It allows a service account to impersonate a Google Workspace user and gain access to the Google data the user has access to, assuming they have provisioned the necessary Authorization scopes to the Service Account.
- No User Consent Required: With DWD, individual user consent is not required. Once the super admin sets up the delegation, the service account can access the specified data of any user in the domain without additional authorization prompts.
- OAuth 2.0 Scopes: When setting up DWD, the super admin specifies which OAuth 2.0 scopes the service account is granted. For instance, they might grant access to the Directory API to allow the service account to read group member data.
- Security: Because DWD grants broad access, it’s essential to handle it with care. The service account’s private key, which is used for authentication, should be kept secure.
Where it is Used
Sysdig’s CIEM analysis requires DWD to provide:
- User and Group Insights derived from Google Workspace and Cloud Identity If DWD is enabled, then Actionable Risk, Excessive Permissions, and Members are displayed on the Identity and Access Groups page.
- Enhanced Monitoring and Reporting for MFA usage, user logins, admin console changes, and third-party application access
- Asset management to gain insights into Roles, Service Accounts, and their associated keys
The onboarding wizard prompts you to perform domain-wide delegation. If you skip this step, you will be prompted again from the Identity and Access (CIEM) page of the Sysdig Secure UI.
Enable Domain-Wide Delegation in GCP
Authorize Service Account Scopes
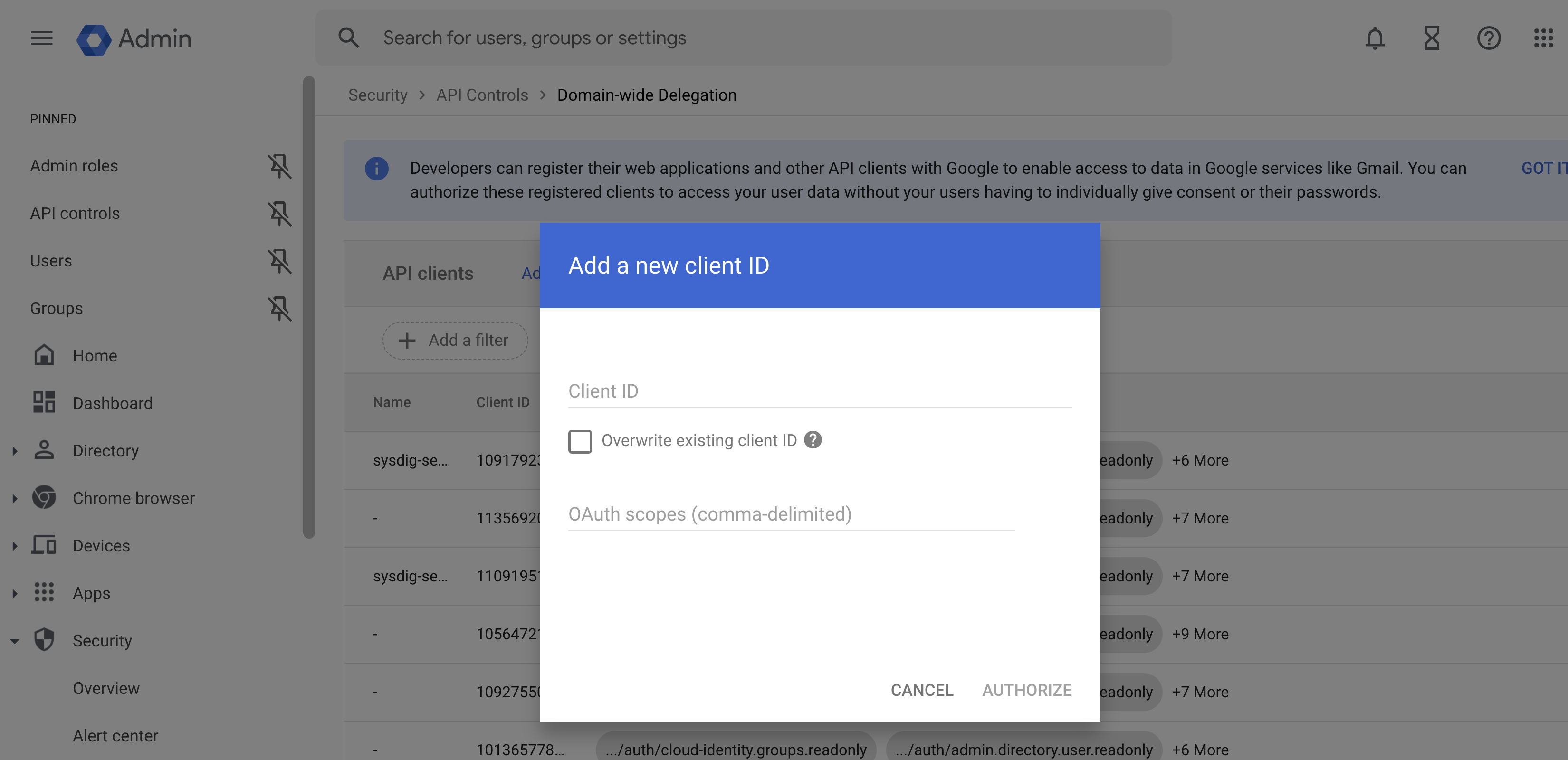
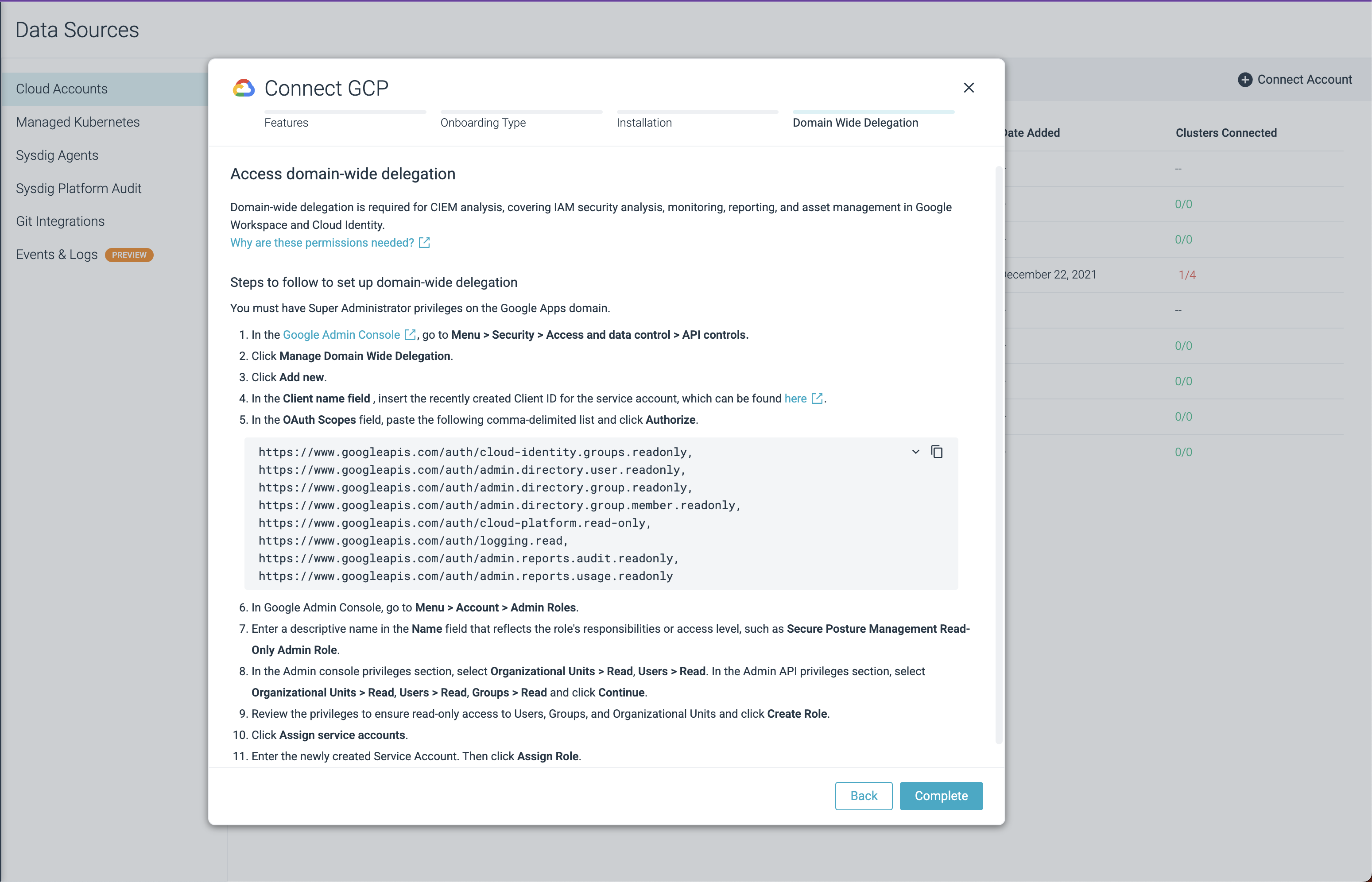
Log in to the Google Admin Console with Super Administrator privileges and select Security > Access and data control > API controls.
Click Manage Domain Wide Delegation.
Click Add New.
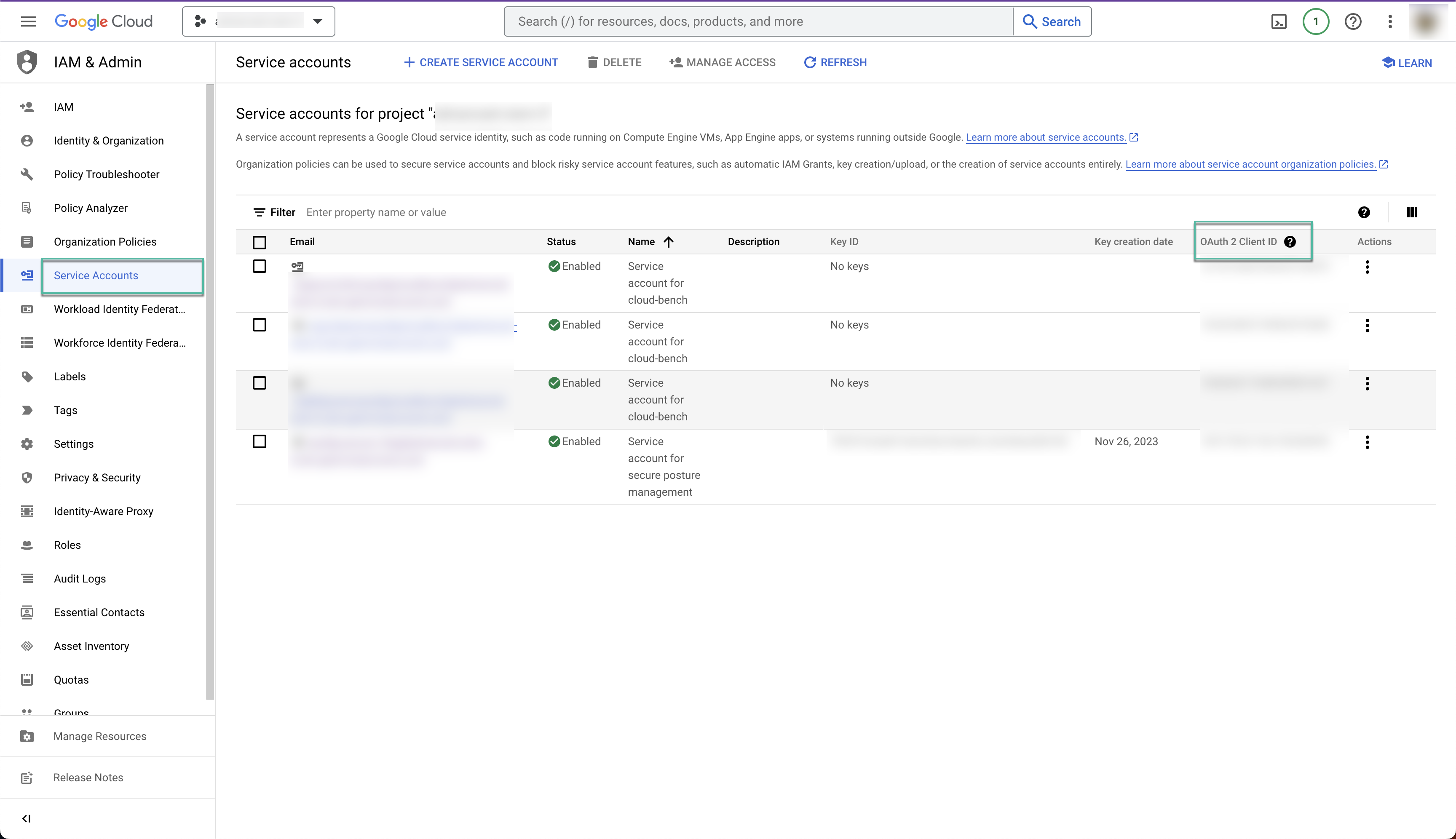
Switch to the Google Cloud Console to collect your service account’s OAuth 2 Client ID:
Navigate to the Project specified during the initial onboarding step.
Select Service Account and search for the newly created Sysdig service account with the format:
sysdig-secure-a1b2@your-project-id.iam.gserviceaccount.com.Click the Service Account link to display the OAuth 2 Client ID and copy it.
Return to the Google Admin Console from Step 3. (Security > Access and data control > API controls > Manage Domain Wide Delegation > Add New ).
In the panel, enter:
Client ID: Paste the OAuth 2 Client ID you copied.
OAuth Scopes: Add the OAuth scopes below in a comma-delimited list.
https://www.googleapis.com/auth/cloud-identity.groups.readonly, https://www.googleapis.com/auth/admin.directory.user.readonly, https://www.googleapis.com/auth/admin.directory.group.readonly, https://www.googleapis.com/auth/admin.directory.group.member.readonly, https://www.googleapis.com/auth/cloud-platform.read-only, https://www.googleapis.com/auth/logging.read, https://www.googleapis.com/auth/admin.reports.audit.readonly, https://www.googleapis.com/auth/admin.reports.usage.readonly,
Click Authorize.
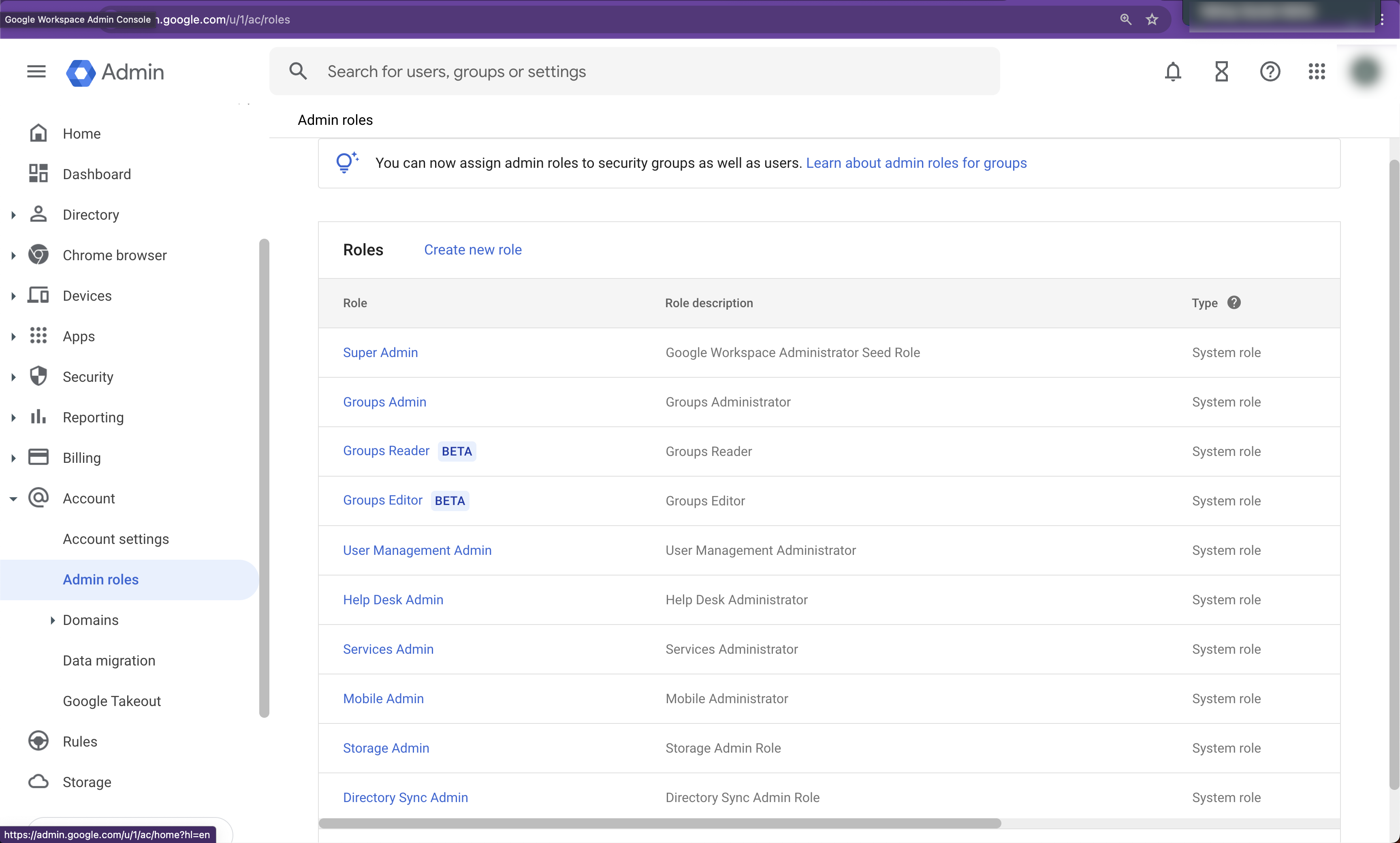
Create a Custom Admin Role and Grant Privileges
While still in the Google Admin Console, go to Account > Admin Roles.
Click Create new role.
Enter the following values:
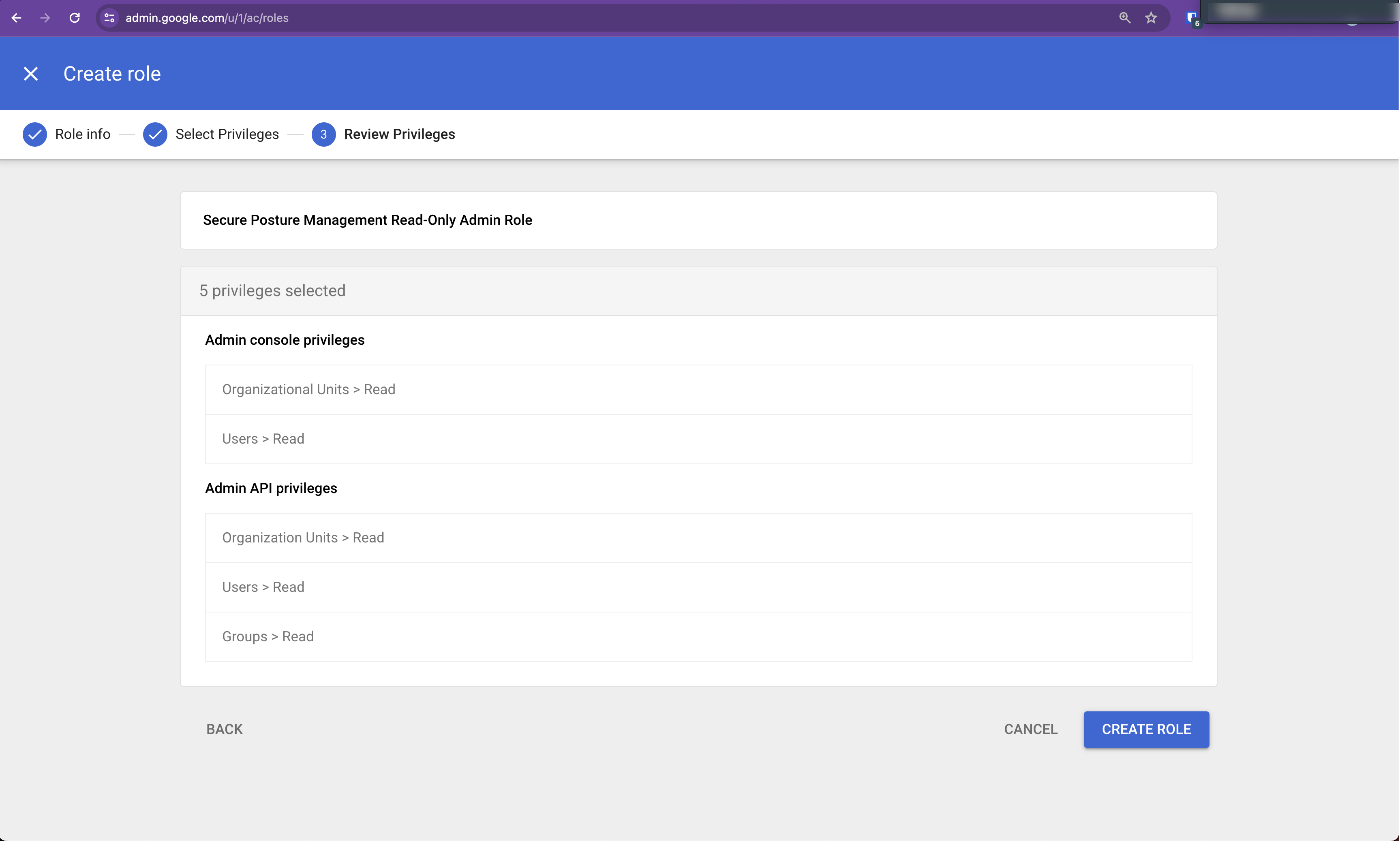
Name: Enter an appropriate name, such as
Secure Posture Management Read-Only Admin Role.Description: Optional
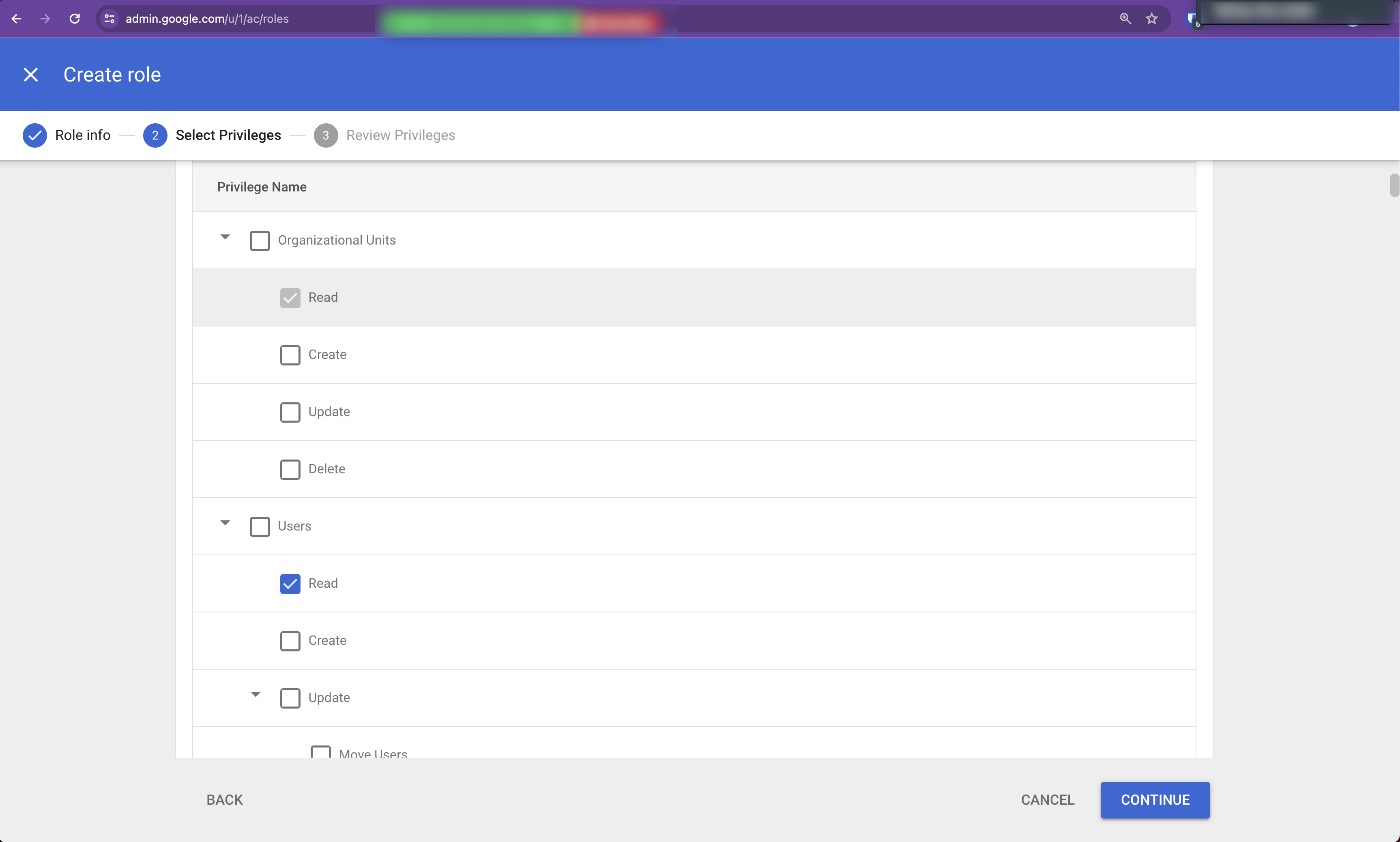
Click Continue. The Select Privileges page appears.
Configure the Select Privileges as follows:
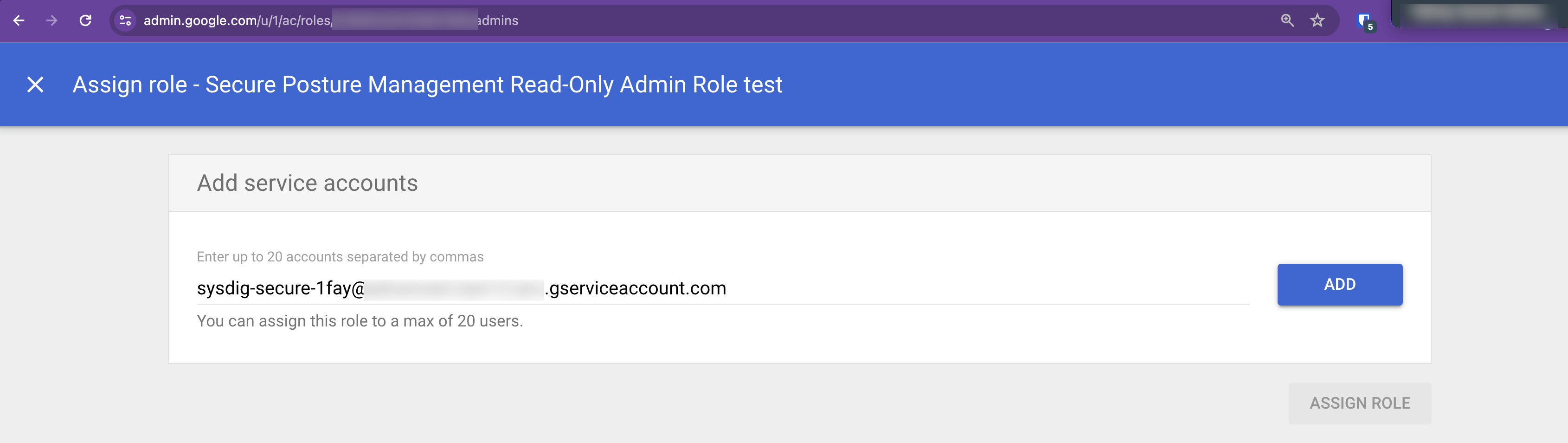
Click Assign Service Accounts.
Enter the Sysdig service account name from step 4 and click Add.
(Format:
sysdig-secure-a1b2@your-project-id.iam.gserviceaccount.com)A confirmation screen is displayed; click Assign Role.
Complete the Sysdig Onboarding Wizard
When all the enablement steps in GCP consoles are complete, return to the Sysdig wizard and click Complete.
Validate
Log in to Sysdig Secure and check that each module you deployed is functioning. It may take 10 minutes or so for events to be collected and displayed.
Check Overall Connection Status
Data Sources: Select Integrations > Data Sources | Cloud Accounts to see all connected cloud accounts.
Check CSPM
Inventory: Select the Inventory module and filter for project =. Check for your GCP cloud account in the drop-down.
Check Identity and Access CIEM (Preview)
Home: Select Home and check the status bar at the top right to see your cloud accounts.
GCP resources are being rolled out for Identity and Access pages, starting with Groups page.
Check Vulnerability Scanning
Check Integrations > Data Sources | Cloud Hosts.
Features and Resources on GCP
Agentless CSPM and Agentless CIEM
Resources Created
google_service_accountgoogle_service_account_keygoogle_project_iam_membergoogle_organization_iam_member(Organizational Installs only)
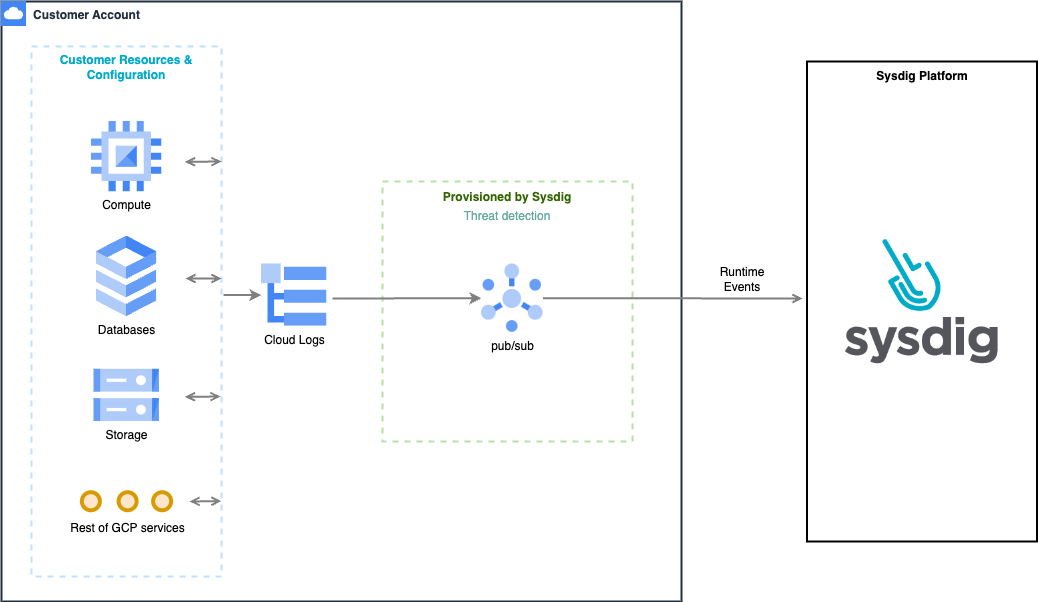
Agentless CDR
Resources Created
google_service_accountgoogle_service_account_iam_bindinggoogle_pubsub_topicgoogle_pubsub_subscriptiongoogle_pubsub_topic_iam_membergoogle_project_iam_audit_config(Single project installs only)google_organization_iam_audit_config(Organizational Installs only)google_logging_project_sink(Single project installs only)google_logging_organization_sink(Organizational Installs only)
Tune the Cloud Logs Volume
When you set up CDR, Sysdig creates a log sink to access logs through Pub/Sub. As a high volume of logs are costly to process, you may wish to tune the number of logs sent to the log sink:
To tune which logs are generated, see Tune Log Generation.
To set up inclusion or exclusion filters, see Tune the Log Sink Filter.
Tuning the configuration will change the logs that will be sent to Sysdig. This will affect Sysdig’s runtime visibility and threat detection capabilities.
Tune audit log generation
CDR enables Data Access audit logs for every service on every connected project by default:
[
{
service = "allServices"
log_config = [
{ log_type = "ADMIN_READ" },
{ log_type = "DATA_READ" },
{ log_type = "DATA_WRITE" }
]
}
]
You can customize this to change the enabled log types or specify the single services. For a the list of services providing audit logs, see the Google Cloud documentation.
To customize this, specify the audit_log_config variable for the -threat-detection module (single-project-threat-detection or organization-threat-detection, depending on the setup). This example snippet enables only data writes for Cloud Storage and everything for Cloud SQL on a single project setup:
module "single-project-threat-detection" {
...
audit_log_config = [
{
service = "storage.googleapis.com"
log_config = [
{ log_type = "DATA_WRITE" }
]
},
{
service = "cloudsql.googleapis.com"
log_config = [
{ log_type = "ADMIN_READ" },
{ log_type = "DATA_READ" },
{ log_type = "DATA_WRITE" }
]
}
]
}
While the Terraform is unique to Sysdig, the configuration affects the project and the logs it generates, which could impact on consumers of those logs. If you want to keep generating these logs, without sending them to Sysdig, you can tune the log filter.
Tune the Log Sink Filter
By default, the log sink filter is configured to only pick up Audit logs: protoPayload.@type = \"type.googleapis.com/google.cloud.audit.AuditLog\". You can add exclusion filters to narrow the scope further.
You can customize the filter by specifying the ingestion_sink_filter in the -threat-detection module, single-project-threat-detection or organization-threat-detection, depending on the setup.
This example snippet excludes get and list methods for Data Access audit logs:
module "single-project-threat-detection" {
...
ingestion_sink_filter = "protoPayload.@type = \"type.googleapis.com/google.cloud.audit.AuditLog\" (protoPayload.methodName !~ \"\\.(get|list)$\" OR logName !~ \"%2Fdata_access$\")"
}
Alternatively you can specify exclude filters with the exclude_logs_filter variable in the same module.
This example excludes:
- gets and lists on kubernetes
- gets and lists on Google Cloud Storage (GCS)
module "single-project-threat-detection" {
...
exclude_logs_filter = [
{
name = "k8s_get_list"
description = "Exclude get and list methods on kubernetes"
filter = "protoPayload.serviceName=\"k8s.io\" and protoPayload.methodName =~ (\"\\.get$\" OR \"\\.list$\")"
},
{
name = "storage_objects_get_list"
description = "Exclude get and list methods on GCS objects"
filter = "protoPayload.methodName = (\"google.storage.objects.get\" or \"google.storage.objects.list\" or \"storage.objects.get\" or \"storage.objects.list\")"
}
]
}
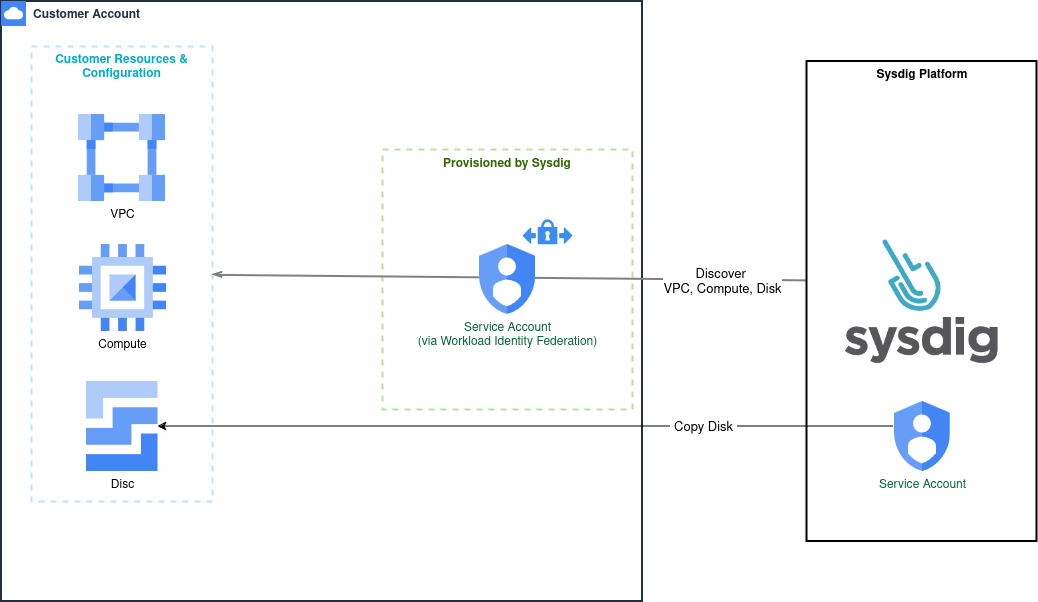
Vulnerability Management Agentless Host Scanning
Resources Created
Note: google_project entries are used for single projects; replace with google_organization for organizaations.
google_iam_workload_identity_poolgoogle_iam_workload_identity_pool_providergoogle_project_iam_custom_rolegoogle_project_iam_bindinggoogle_service_accountgoogle_service_account_iam_memberx2, to bind service_account to a custom and existing role
Host Scanning authentication involves fetching the opted-in instance disks:
google_project_iam_bindinggoogle_project_iam_custom_role
See also the VM Host Scanning Terraform Readme.
How to Exclude/Include Resources from Vulnerability Scanning
When you connect a GCP project with Vulnerability Host Scanning, by default all Compute Instances with root volumes in the project are included in the scan.
If you need to exclude specific Compute Instances from being scanned, you can do so using tags.
How to exclude Instances: To exclude certain Compute Instances from being scanned, you must assign specific tags to them in the GCP Console or using GCP APIs.
It is recommended to set these tags before initiating the scanning process. You can add tags after onboarding, but note that the exclusion will only take effect in subsequent scans.
How to include Data Volumes in Scans: By default, only root volumes of Compute Instances are scanned.
To also include data volumes in scans, you need to use the specific tags declared below.
Tagging Semantics
You can use the following tags at Volume or Compute Instance level. Tagging can be added at any time, for example, if you want to exclude/include something that was or was not scanned.
Key: sysdig-secure-scan, sysdig-secure-data-volumes-scan.
Values: true, false
Usage Examples
“sysdig-secure-scan” : “false”on a Compute Instance excludes the instance and all its volumes from scanning;“sysdig-secure-scan” : “true”on a data-volume of a Compute Instance includes such volume for scanning;“sysdig-secure-data-volumes-scan” : “true”on a Compute Instance has the same effect as applying the“sysdig-secure-scan” : “true”tag to all its data-volumes.
The following tags are redundant; using them will have the same effect as not having them. This is either because Sysdig scans them by default or because the values have been overridden by a tag at a higher level (such as a Compute Instance).
“sysdig-secure-scan” : “true”on a Compute Instance;“sysdig-secure-scan” : “true”on the root volume of a Compute Instance;“sysdig-secure-scan” : “false”on any data-volumes of a Compute Instance;“sysdig-secure-scan” : “false”on the root volume of a Compute Instance has no effect. The root volume is always scanned as part of the Compute Instance scan;“sysdig-secure-data-volumes-scan” : “false”on a Compute Instance;“sysdig-secure-data-volumes-scan” : “false”on any data-volumes of a Compute Instance.
Learn More
Feedback
Was this page helpful?
Glad to hear it! Please tell us how we can improve.
Sorry to hear that. Please tell us how we can improve.