Terraform Provider
Sysdig provides a Terraform Provider to expose and use some of the most common Sysdig API functions for
- Sysdig Platform
- Sysdig Secure
- Sysdig Monitor
Learn more about using the provider in the official Terraform Registry - Sysdig Provider repository.
You can also provide feedback or create pull requests in the Sysdig Terraform Provider Source Github Repository
Using Terraform
Terraform is a tool for building, changing, and versioning infrastructure safely and efficiently. Terraform can manage existing and popular service providers as well as custom in-house solutions.
Configuration files describe to Terraform the components needed to run a single application or your entire datacenter. Terraform generates an execution plan describing what it will do to reach the desired state, and then executes it to build the described infrastructure or configuration.
As the configuration changes, Terraform is able to determine what changed and create incremental execution plans which can be applied.
Terraform Provider for Sysdig
The Terraform Provider for Sysdig allows you to manage your configuration in Sysdig Secure and Sysdig Monitor as code, allowing you to synchronize your declarative configuration with the configuration at the Platform.
You can instrument several use cases like:
- Backup/restore
- Disaster recovery
- Configuration version management
Installation
Follow Terraform Registry - Sysdig Provider official instructions.
Create Resources with Terraform
This is an example to create a pair of rules able to detect SSH connections and shells spawned in containers.
Define a couple of rules in the
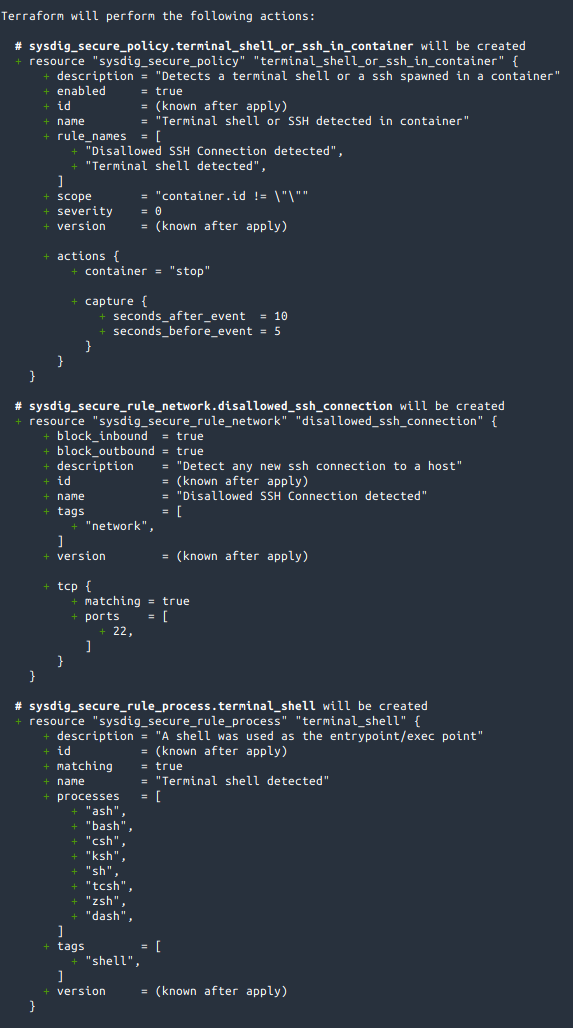
rules.tffile. One rule to detect inbound and outbound connections made to the port 22, and the other to detect a shell process being spawned.resource "sysdig_secure_rule_network" "disallowed_ssh_connection" { name = "Disallowed SSH Connection detected" description = "Detect any new ssh connection to a host" tags = ["network"] block_inbound = true block_outbound = true tcp { matching = true ports = [22] } } resource "sysdig_secure_rule_process" "terminal_shell" { name = "Terminal shell detected" description = "A shell was used as the entrypoint/exec point" tags = ["shell"] processes = ["ash", "bash", "csh", "ksh", "sh", "tcsh", "zsh", "dash"] }For more information about the configuration blocks, see Terraform Syntax.
Create a policy in a file called
policy.tfto define how these rules are applied. The policy will stop the affected container and trigger a capture for further troubleshooting.resource "sysdig_secure_policy" "terminal_shell_or_ssh_in_container" { name = "Terminal shell or SSH detected in container" description = "Detects a terminal shell or a ssh spawned in a container" enabled = true severity = 0 // HIGH scope = "container.id != \"\"" rule_names = [sysdig_secure_rule_network.disallowed_ssh_connection.name, sysdig_secure_rule_process.terminal_shell.name] actions { container = "stop" capture { seconds_before_event = 5 seconds_after_event = 10 } } }With the given
scope, the policy will only be applied to processes being executed inside containers:scope = "container.id != \"\""Perfrom
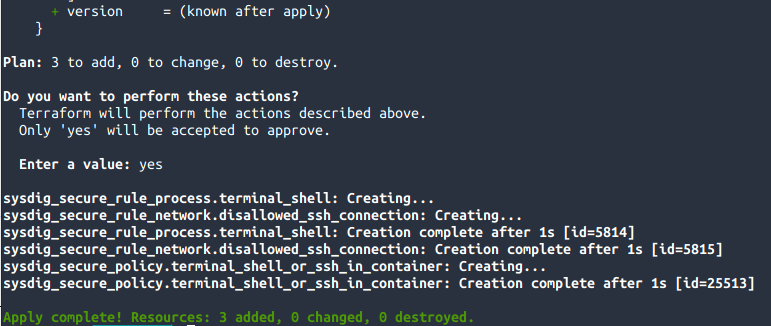
terraform apply.Using
terraform applythe resources are applied in the backend:Terraform reports that three resources will be created, which matches what you defined in
rules.tfandpolicy.tf.After applying the plan, ensure that Terraform reports about the resource creation.
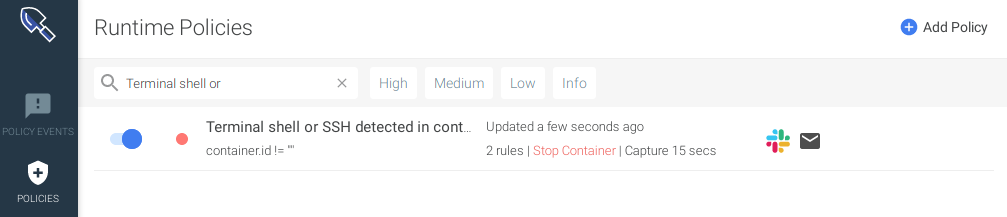
The policy uses the rules created before, therefore, it’s the last one being created.
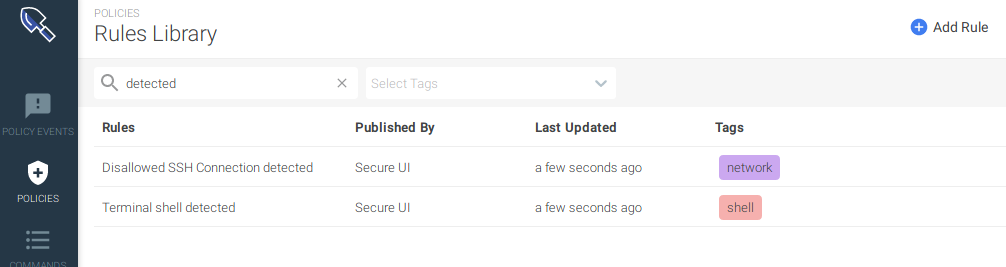
When the resources have been created, they appear as follows in the Sysdig Secure UI.
However, if this policy triggers no alert notification unless you create notification channels.
Create two notification channels, one for the email and another one for slack in a file called
notification.tf.resource "sysdig_secure_notification_channel_email" "devops-email" { name = "DevOps e-mail" enabled = true recipients = "devops@example.com" notify_when_ok = false notify_when_resolved = false } resource "sysdig_secure_notification_channel_slack" "devops-slack" { name = "DevOps Slack" enabled = true url = "https://hooks.slack.com/services/xyz" channel = "#devops" notify_when_ok = false notify_when_resolved = false }They will alert when the policy is triggered.
Bind them to the policy by modifying the
policy.tffile. Note thenotification_channelsproperty:resource "sysdig_secure_policy" "terminal_shell_or_ssh_in_container" { name = "Terminal shell or SSH detected in container" description = "Detects a terminal shell or a ssh spawned in a container" enabled = true severity = 0 // HIGH scope = "container.id != \"\"" rule_names = [sysdig_secure_rule_network.disallowed_ssh_connection.name, sysdig_secure_rule_process.terminal_shell.name] actions { container = "stop" capture { seconds_before_event = 5 seconds_after_event = 10 } } notification_channels = [sysdig_secure_notification_channel_email.devops-email.id, sysdig_secure_notification_channel_slack.devops-slack.id] }Perform
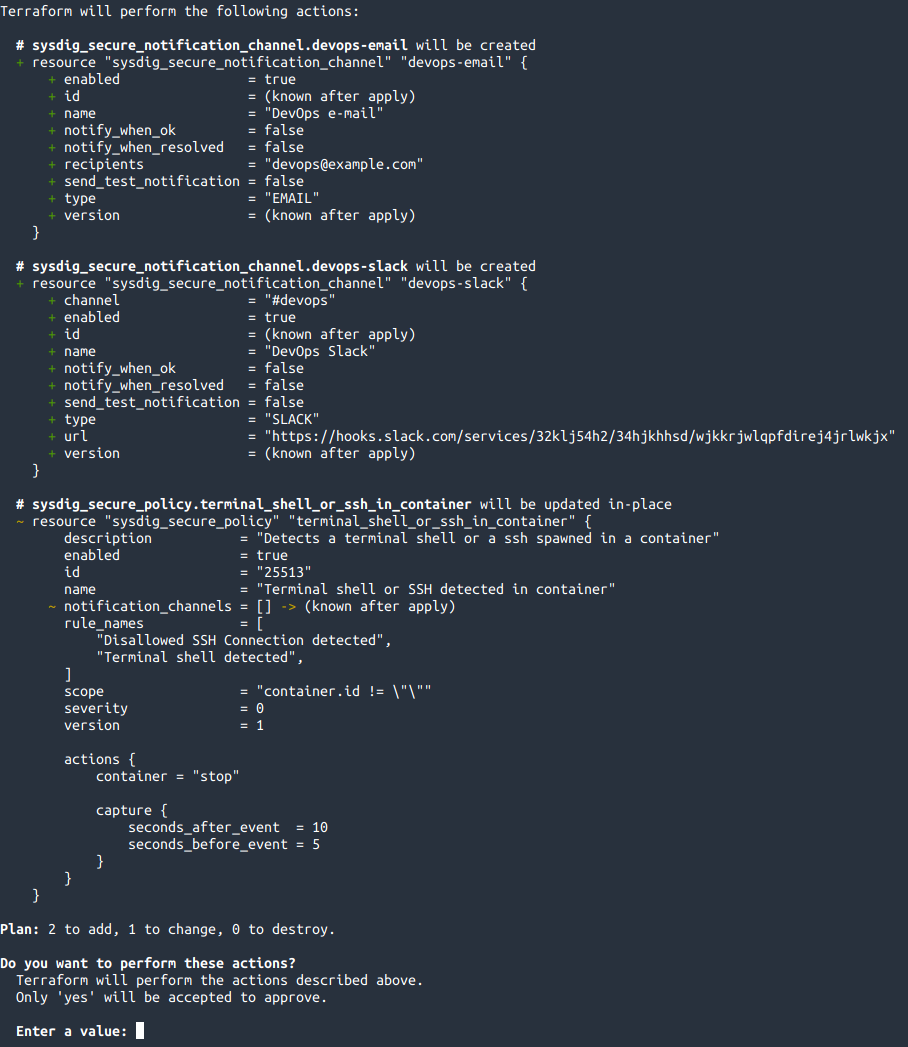
terraform apply.Terraform will create two new resources and modify the existing policy
Choose yes.
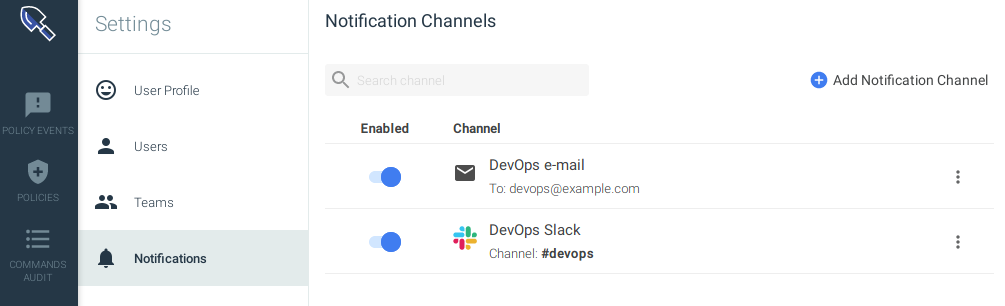
Terraform will create the notification channels and bind them to the policy, ensuring that the state in Monitor and Secure matches our state defined in the code.
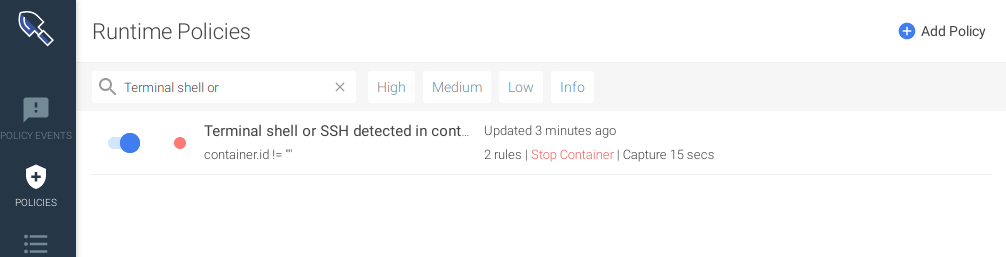
This is how the resources appear on the Sysdig Secure UI:
Now, if you try to update it manually, by re-applying the policies, Terraform will restore the desired status from the .tf manifests.
Learn More
Check all the available resources and datasources for the Terraform Provider for Sysdig in the official Terraform Registry.
Feedback
Was this page helpful?
Glad to hear it! Please tell us how we can improve.
Sorry to hear that. Please tell us how we can improve.