Configure Okta for OIDC
Prerequisites
Sysdig
- Review OpenID Connect (SaaS).
Okta
Review the Prerequisites.
Administrative privileges
Configure an OIDC - OpenID Connect Web application separately for each Sysdig product: Sysdig Monitor and Sysdig Secure.
For more information, see Setting Up an OpenID Connect Application in Okta.
The topics below call out specific steps that require additional action.
Configure Okta
This topic describes the minimal configuration options in Okta. You may need to adjust them based on the specifics of your environment.
General Settings
Specify the application name, and optionally, add a logo.
If you don’t intend to configure the IdP-initiated login flow, select Do not display application icon to users and Do not display application icon in the Okta Mobile app.
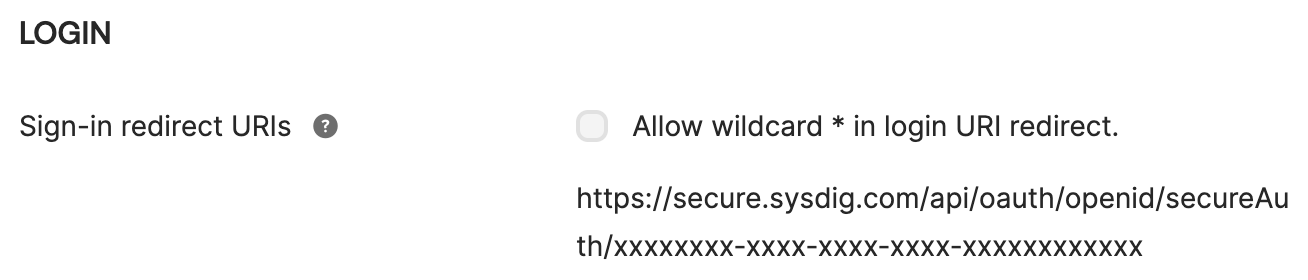
Login
Make sure to disable option Allow wildcard * in login URI redirect.
Identify the correct Sign-in redirect URI associated with your Sysdig application and region. Enter the value in the field for Sign-in redirect URI. Click Save.
See Redirect URI section for more information.
This is the callback URL to which Okta sends the authentication response and ID token when an user attempts to log in to Sysdig using SSO.
Parameters Required for Sysdig Configuration
Copy the following for the OpenID configuration parameters in the Sysdig authentication settings.
- Client ID: Copy the value from the Client Credentials section on the General tab.
- Client Secrets: Copy the Client Secrets from the General tab.
- Issuer URL: Copy the value from the OpenID Connect ID Token section on the Sign On tab.
Configure Sysdig Settings
To enable Okta OpenID functionality on the Sysdig application, specify the following:
| Configuration | Description |
|---|---|
| Client ID | Specify the value you have copied from the Client Credentials section on the General tab. |
| Client Secret | Specify the value you have copied from the Client Secrets section on the General tab. |
| Issuer URL | Specify the value you have copied from the OpenID Connect ID Token section on the Sign On tab. |
| Base Issuer | The value is your Okta domain name. For example, https://myOktaOrg.okta.com |
| Authorization Endpoint | To view the metadata tied to your Okta application, including the Authorization Endpoint, use the following endpoint.https://{myOktaOrg}/.well-known/openid-configuration?client_id={ClientId}Replace {myOktaOrg} with your Okta domain name and {ClientId} with the Client ID associated with your Okta web application. |
{
issuer: "https://myOktaOrg.okta.com",
authorization_endpoint: "https://myOktaOrg.okta.com/oauth2/v1/authorize",
token_endpoint: "https://myOktaOrg.okta.com/oauth2/v1/token",
userinfo_endpoint: "https://myOktaOrg.okta.com/oauth2/v1/userinfo",
registration_endpoint: "https://myOktaOrg.okta.com/oauth2/v1/clients/<redacted>",
jwks_uri: "https://myOktaOrg.okta.com/oauth2/v1/keys?client_id=<redacted>",
<redacted>
```|
Feedback
Was this page helpful?
Glad to hear it! Please tell us how we can improve.
Sorry to hear that. Please tell us how we can improve.